AttackDefense.com [SXSS] - YetiForce CRM
Mission
In this exercise, the attacker has admin access already so there is nothing more to be done. However, looks like the admin access does lead to an XSS attack. So you can try to find this XSS as purely academic exercise.
A version of YetiForce CRM is vulnerable to stored cross side scripting attack. The following username and passwords may be used to explore the application and/or find a vulnerability which might require authenticated access:
- Username: admin
- Password: Password1
Objective: Your task is to find and exploit this vulnerability.
Level difficulty: Easy
Category: Real World Webapps > Stored XSS
Solution
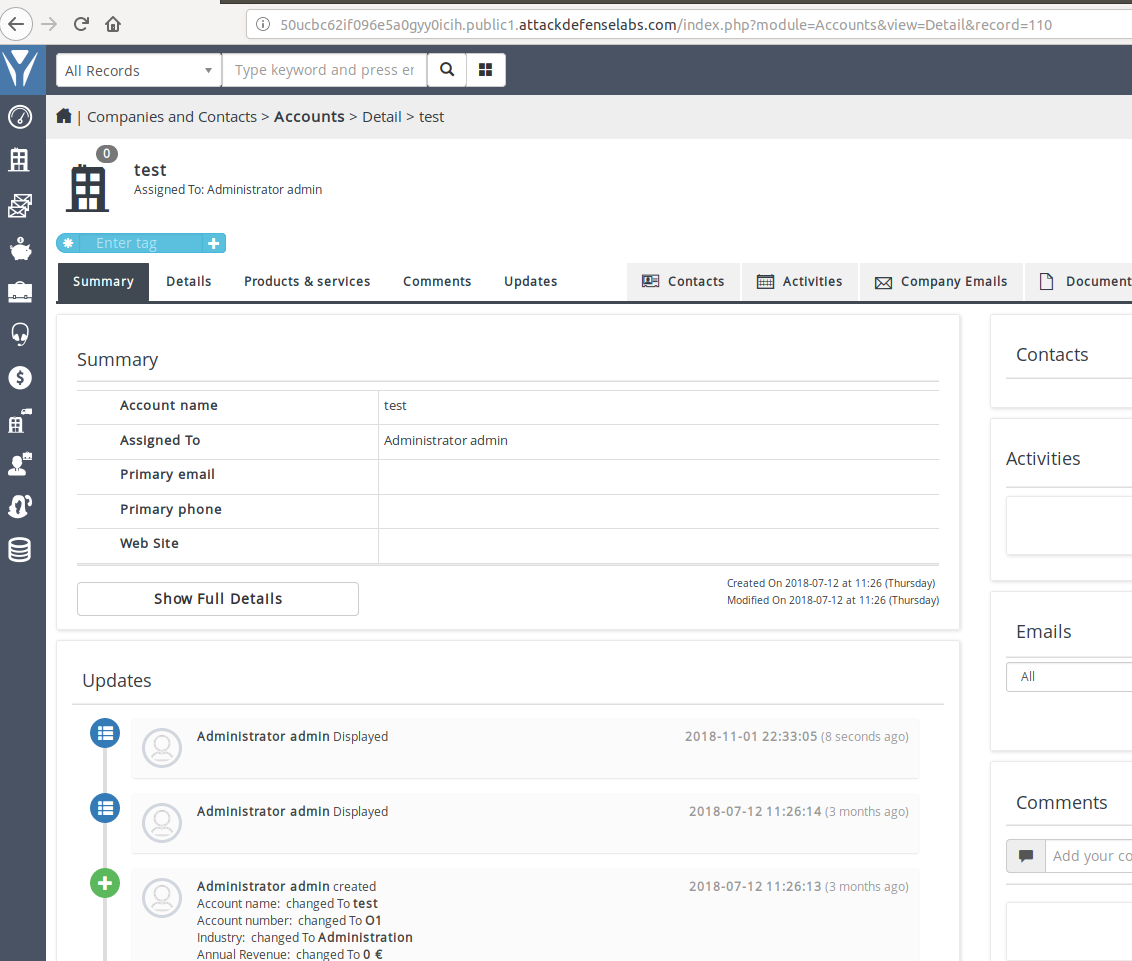
At first, I was prompted straight to the application login and by using the above-provided username and password. I was able to gain access to the application backend.
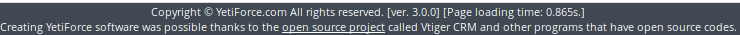
Straight after login, we can see that in the footer section of the application the version is listed as 3.0.0.
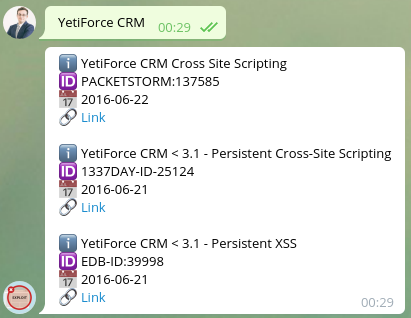
Not knowing from where to start, I decided to use @GetSploitBot for Telegram in order to obtain exploits for the provided information “A version of YetiForce CRM is vulnerable to stored cross side scripting attack.”.
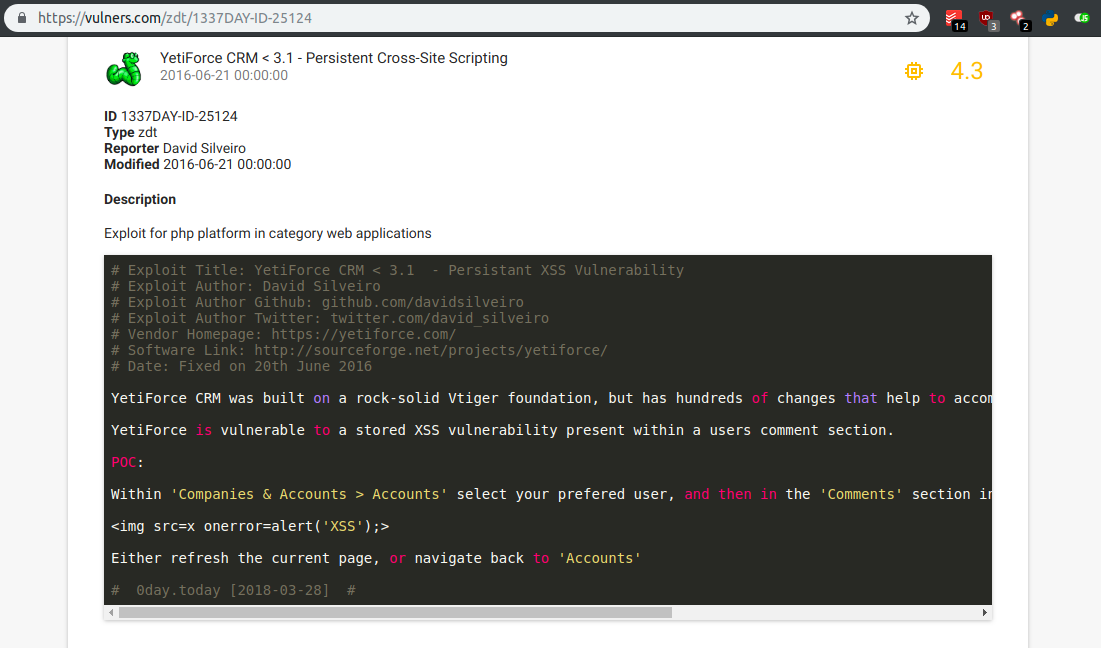
Accessing the following link we can observe the exploit described path and input field.
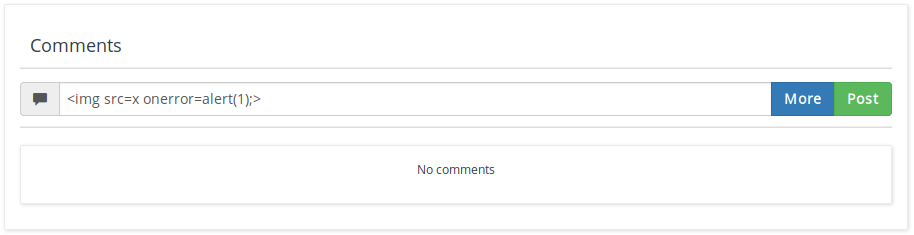
I set my payload as such in the comments input:
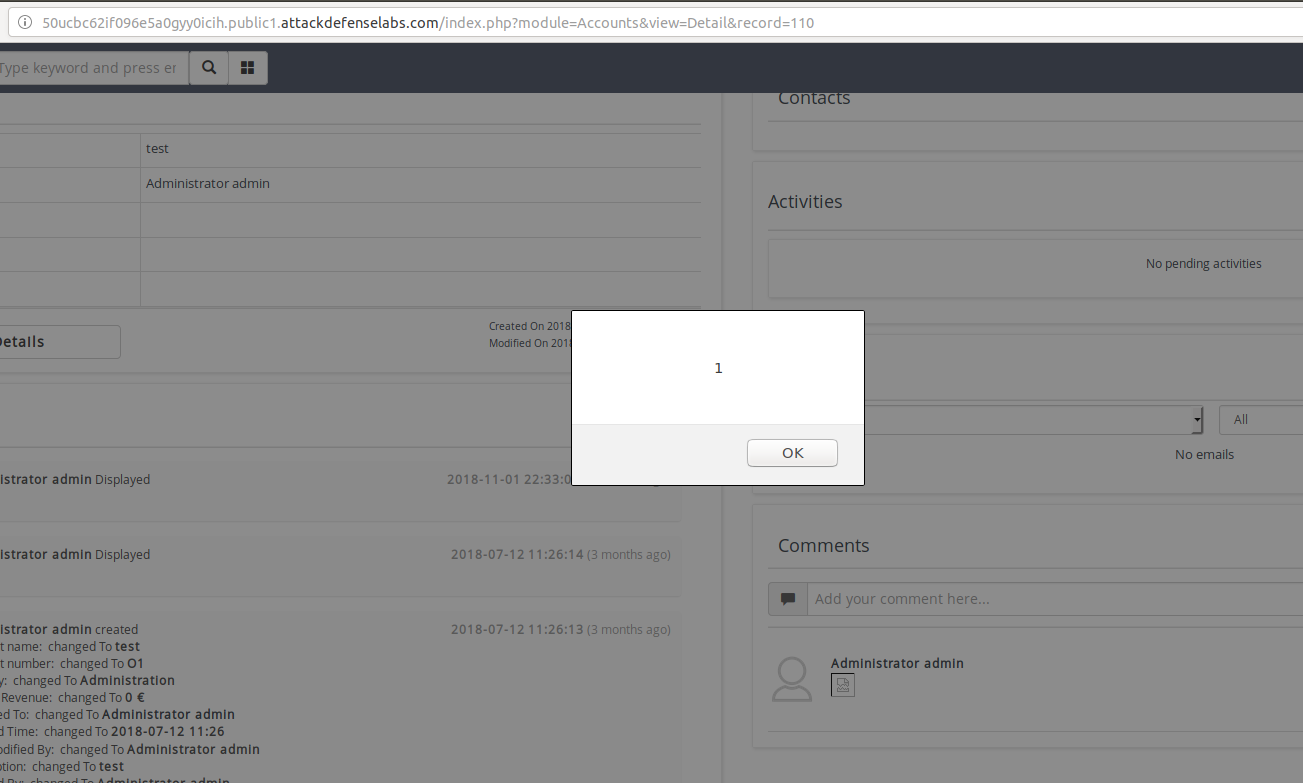
Proof of Stored XSS: