AttackDefense.com [SXSS] - MyBB Downloads Plugin
Mission
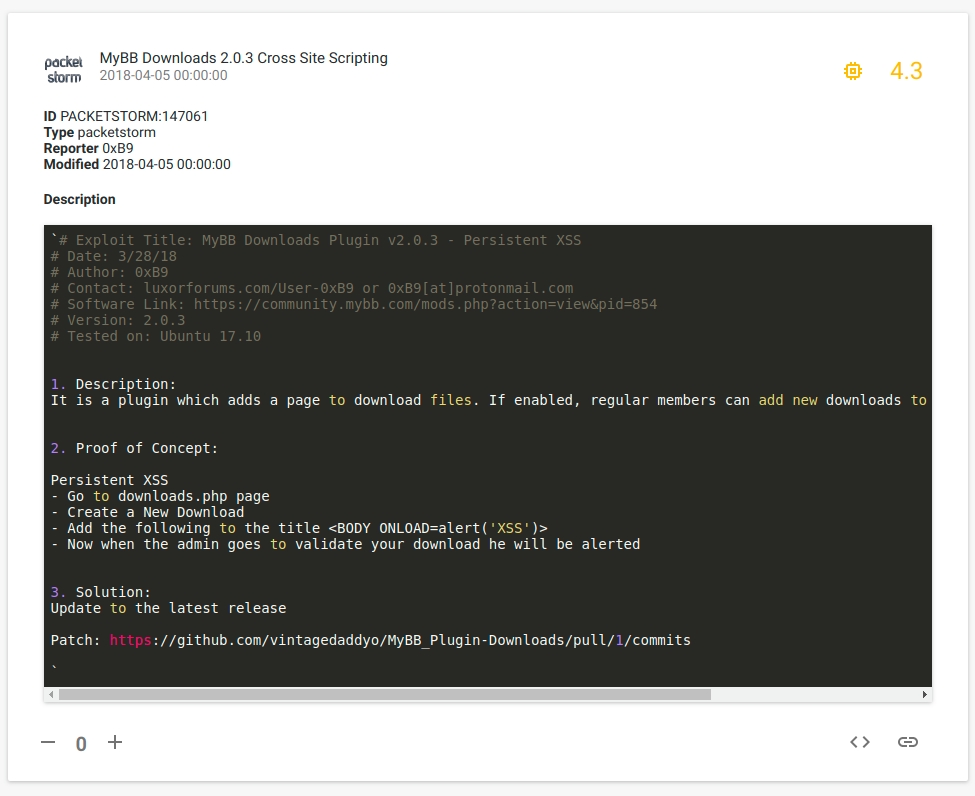
A version of MyBB Downloads Plugin is vulnerable to a stored cross site scripting attack.Your task is to find and exploit this vulnerability.
The following username and password may be used to explore the application and create regular users if required to exploit authenticated access vulnerabilities:
- User: test2
- Password: password
Level difficulty: Easy
Category: Real World Webapps > Stored XSS
Solution
On this challenge, I received a real MyBB forum application deployment and potentially at the last available version.
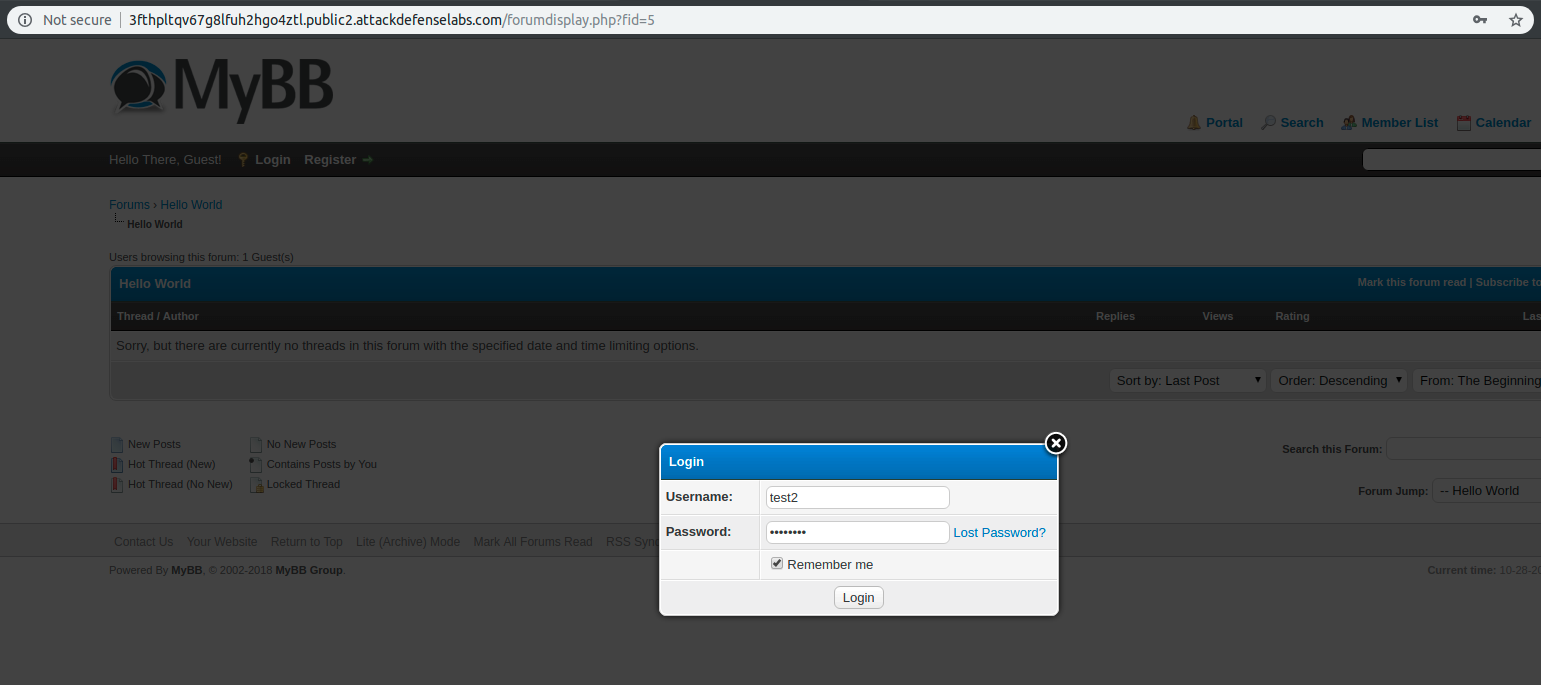
I used the above-provided credentials to authenticate on the forum application:
At this point, we discover that the provided credentials are for an unprivileged user (forum member).
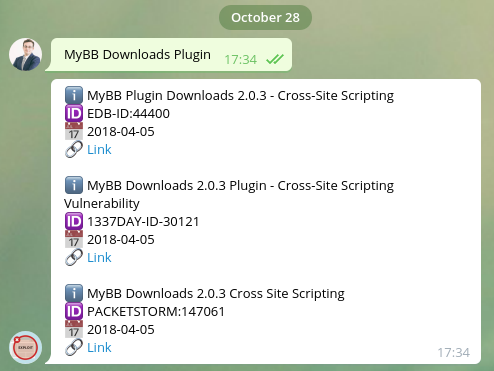
Not knowing from where to start, I decided to use @GetSploitBot for Telegram in order to obtain exploits for the provided information “A version of MyBB Downloads Plugin is vulnerable”.
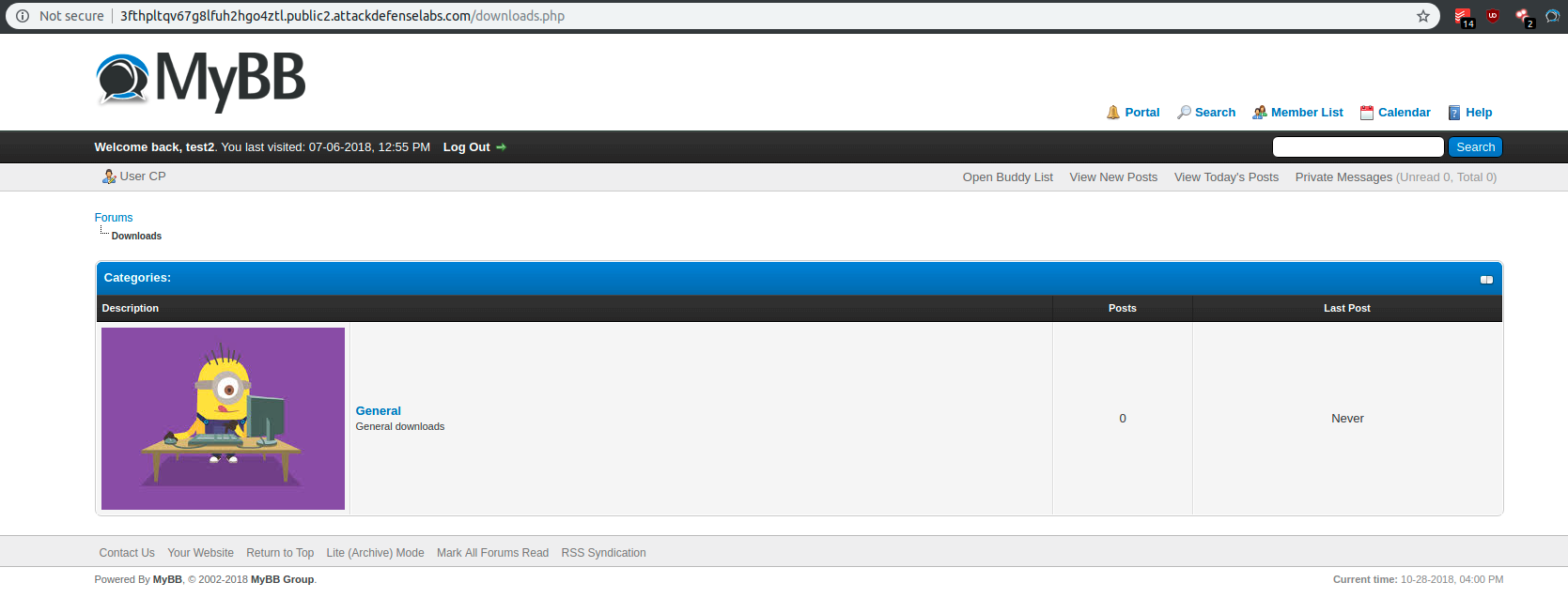
By going to http://3fthpltqv67g8lfuh2hgo4ztl.public2.attackdefenselabs.com/downloads.php I discovered the following Minion.
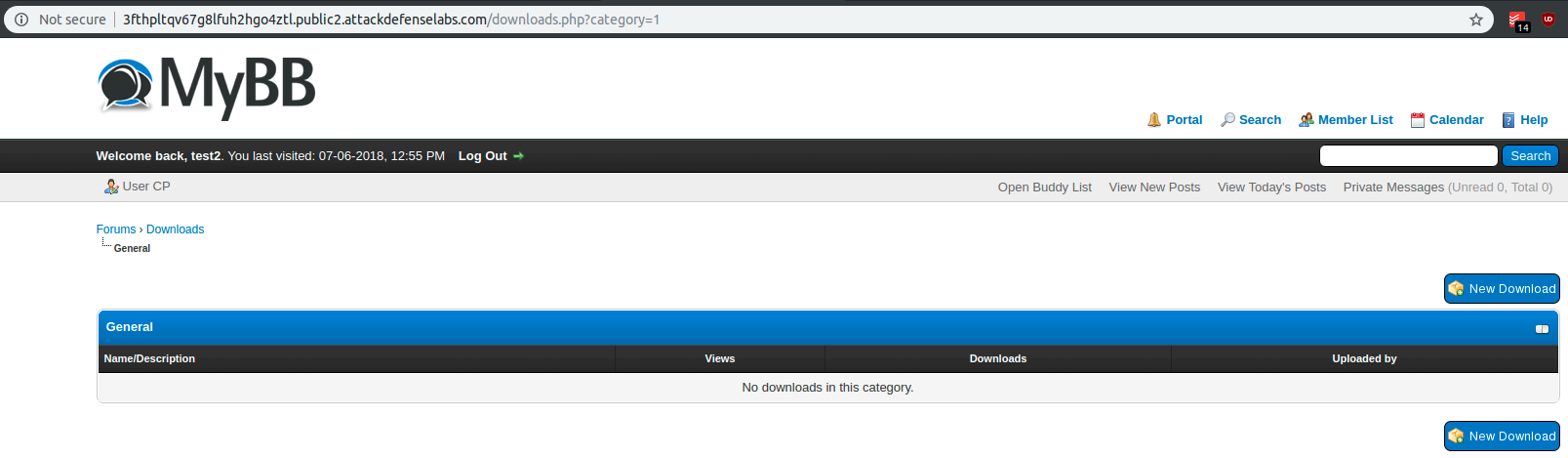
By accessing that specific Minion (http://3fthpltqv67g8lfuh2hgo4ztl.public2.attackdefenselabs.com/downloads.php?category=1), I discovered the place where I should proceed with the exploit steps.
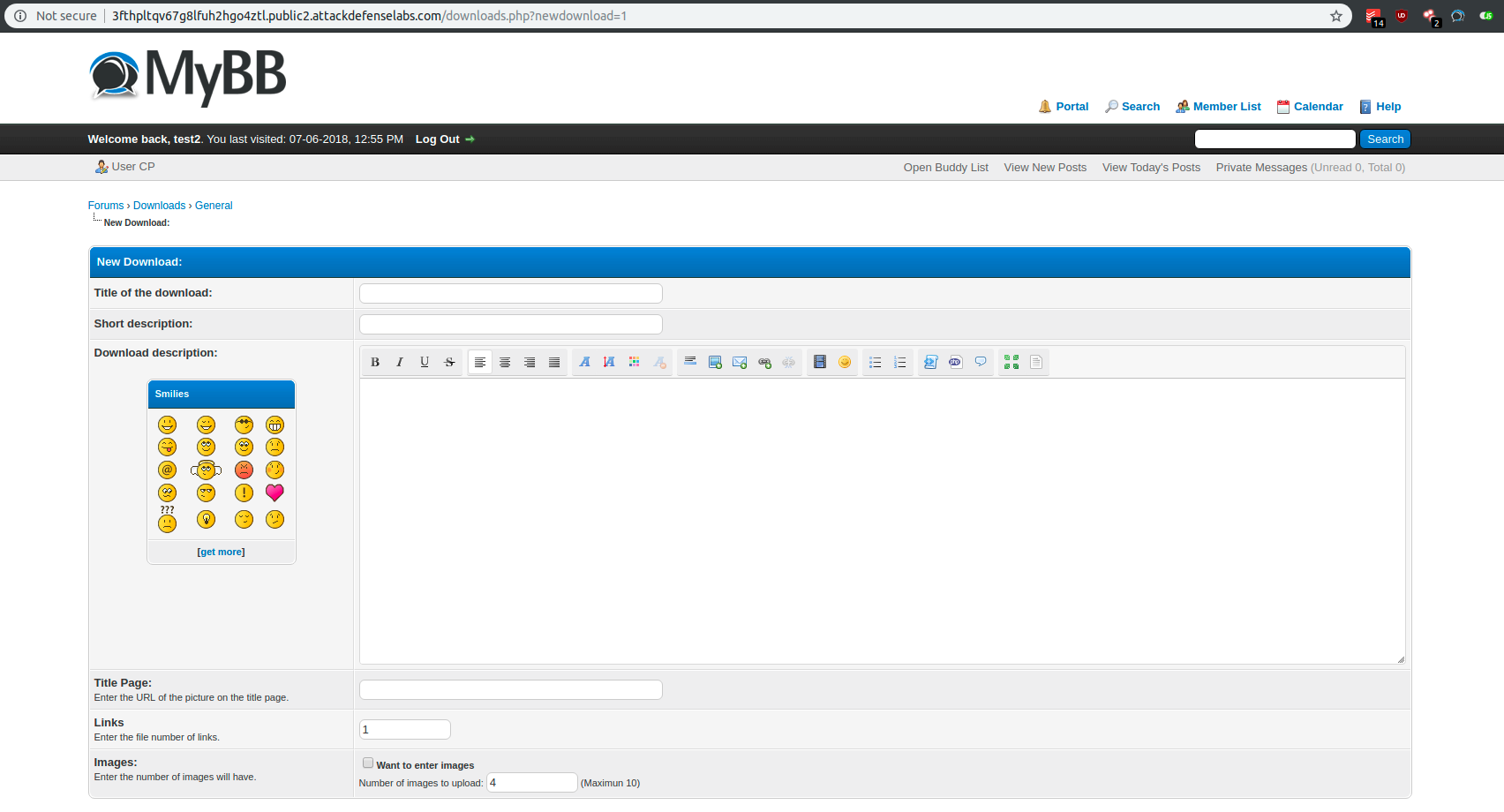
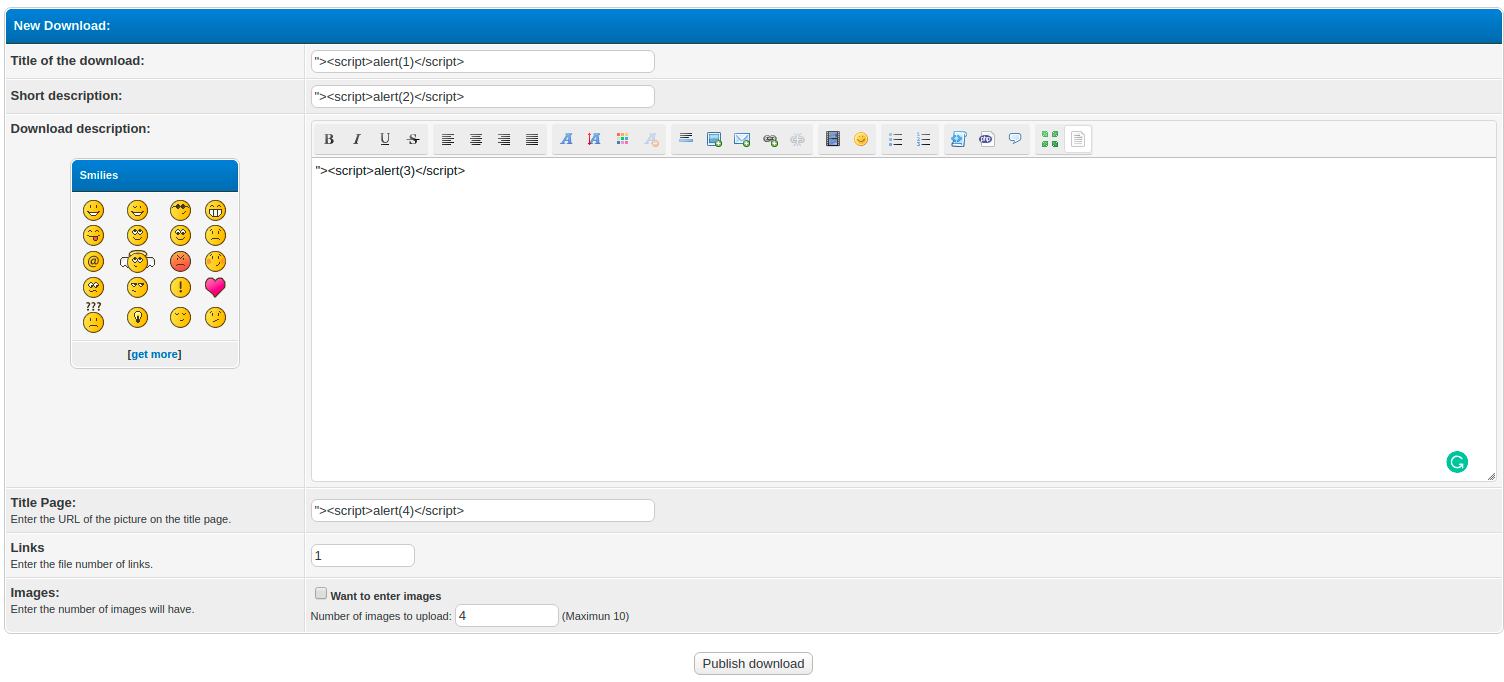
By clicking on “New Download”, I was redirected to http://3fthpltqv67g8lfuh2hgo4ztl.public2.attackdefenselabs.com/downloads.php?newdownload=1.
I introduced multiple payloads in order to test for other XSS vulnerabilities then described on the reported exploit.
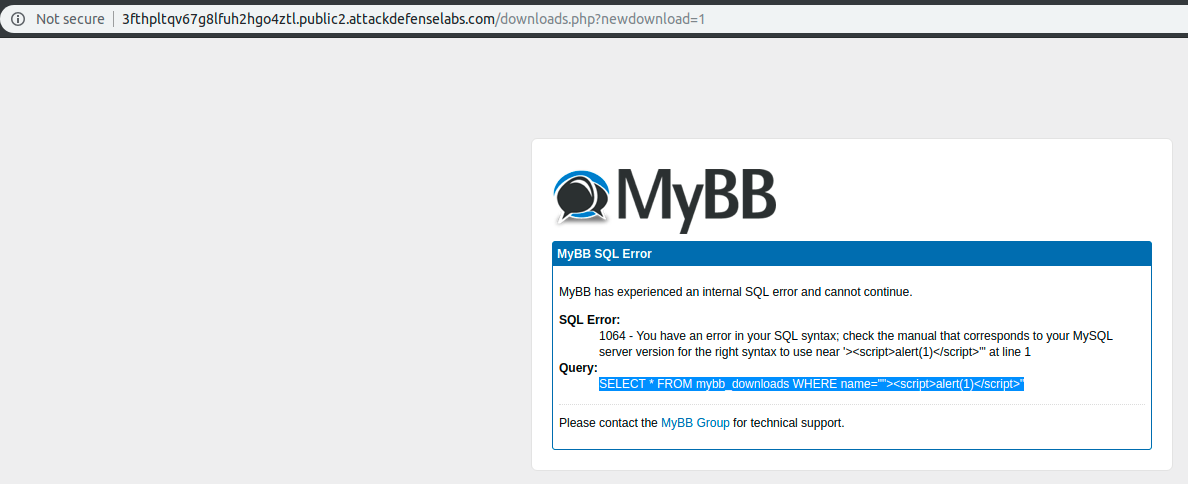
Funny enough I was unable to exploit my XSS due to the fact that I created an unintended SQL Injection exploit (OPS… my bad!). Also at the moment of this article, the identified SQL Injection vulnerability has no public available exploit (yet another Zero-day?).
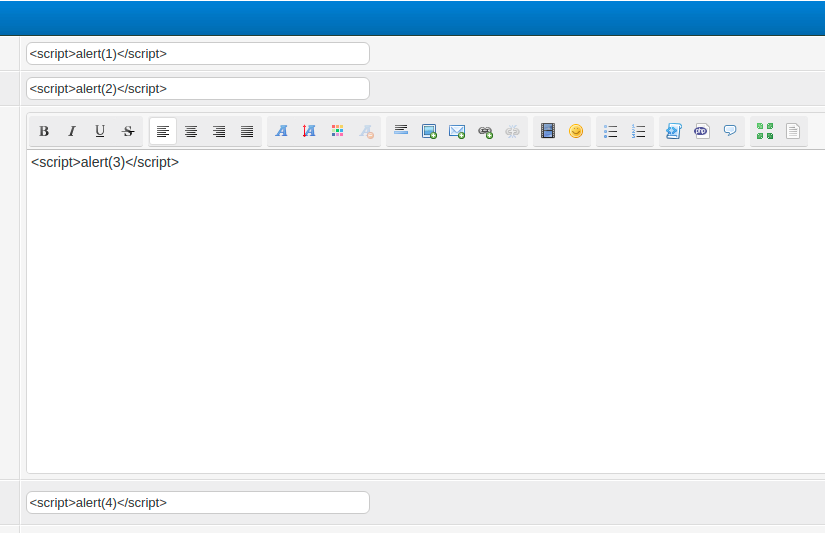
I changed my XSS payloads as such:
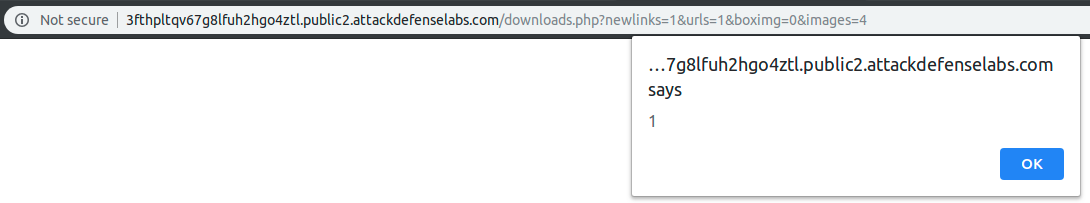
And I obtained my XSS payload that can be traced back to my payload input: