AttackDefense.com [SXSS] - ApPHP MicroBlog
Mission
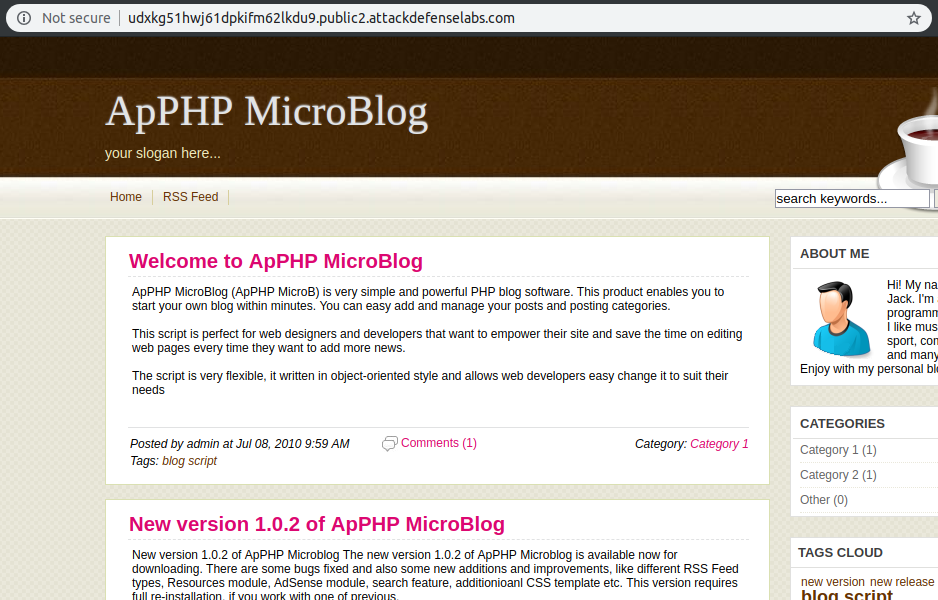
A version of ApPHP MicroBlog is vulnerable to stored cross site scripting attack. Your task is to find and exploit this vulnerability. Authenticated access is not required to exploit this vulnerability.
Level difficulty: Easy
Category: Real World Webapps > Stored XSS
Solution
On this challenge, I was again provided with the same version of ApPHP MicroBlog as on the RCE exercise found here.
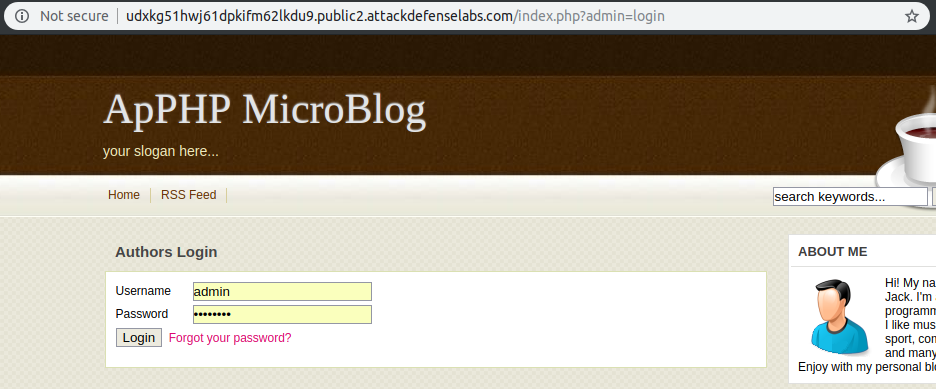
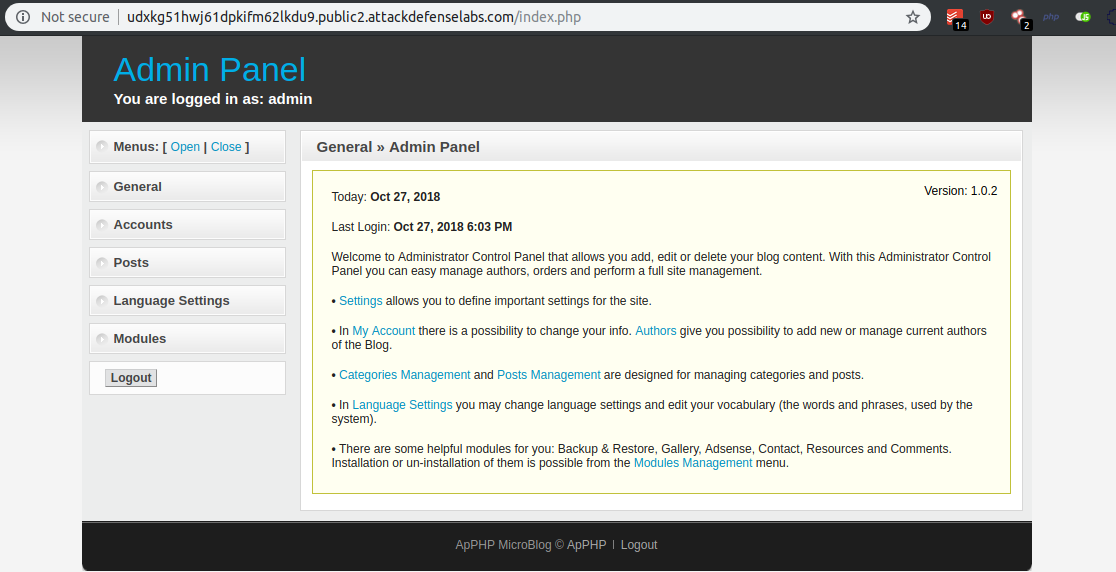
Therefore, I tried the same password and username (admin && password) as in the RCE challenge on the admin login form.
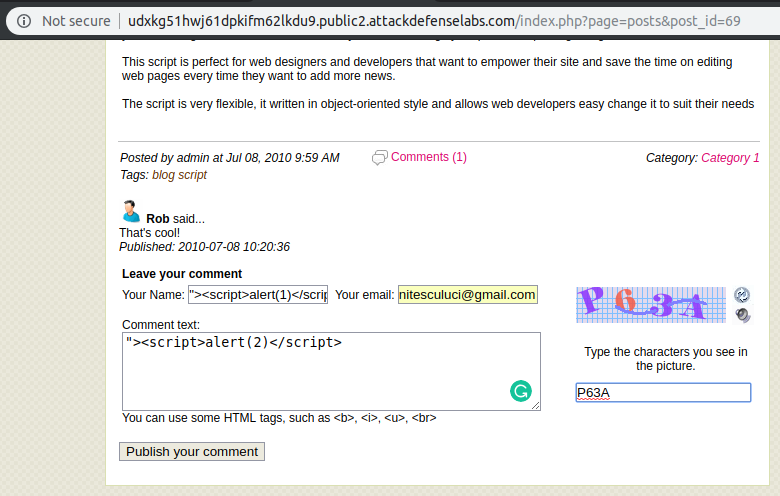
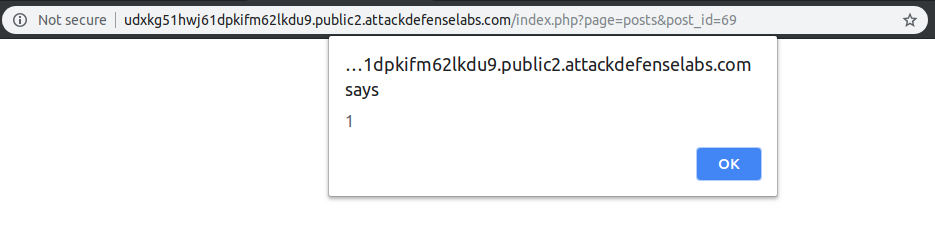
By going to an already posted article, we can observe the presence of a comment module within our blog. In that comment module, I used the following examples of XSS payloads.
With a simple refresh I have obtained the following result:
This post is licensed under CC BY 4.0 by the author.