AttackDefense.com [SXSS] - Concrete5 CMS
Mission
In this exercise, the attacker has admin access already so there is nothing more to be done. However, looks like the admin access does lead to an XSS attack. So you can try to find this XSS as purely academic exercise.
A version of Concrete5 CMS is vulnerable to a stored cross site scripting attack. The following username and passwords may be used to explore the application and/or find a vulnerability which might require authenticated access:
- Username: admin
- Password: 123321
Objective: Your task is to find and exploit this vulnerability.
Level difficulty: Easy
Category: Real World Webapps > Stored XSS
Solution
This time, I was provided with a full Concrete5 CMS website with multiple pages.
On the following page, I found the admin panel login and, I got access using the provided username and password.
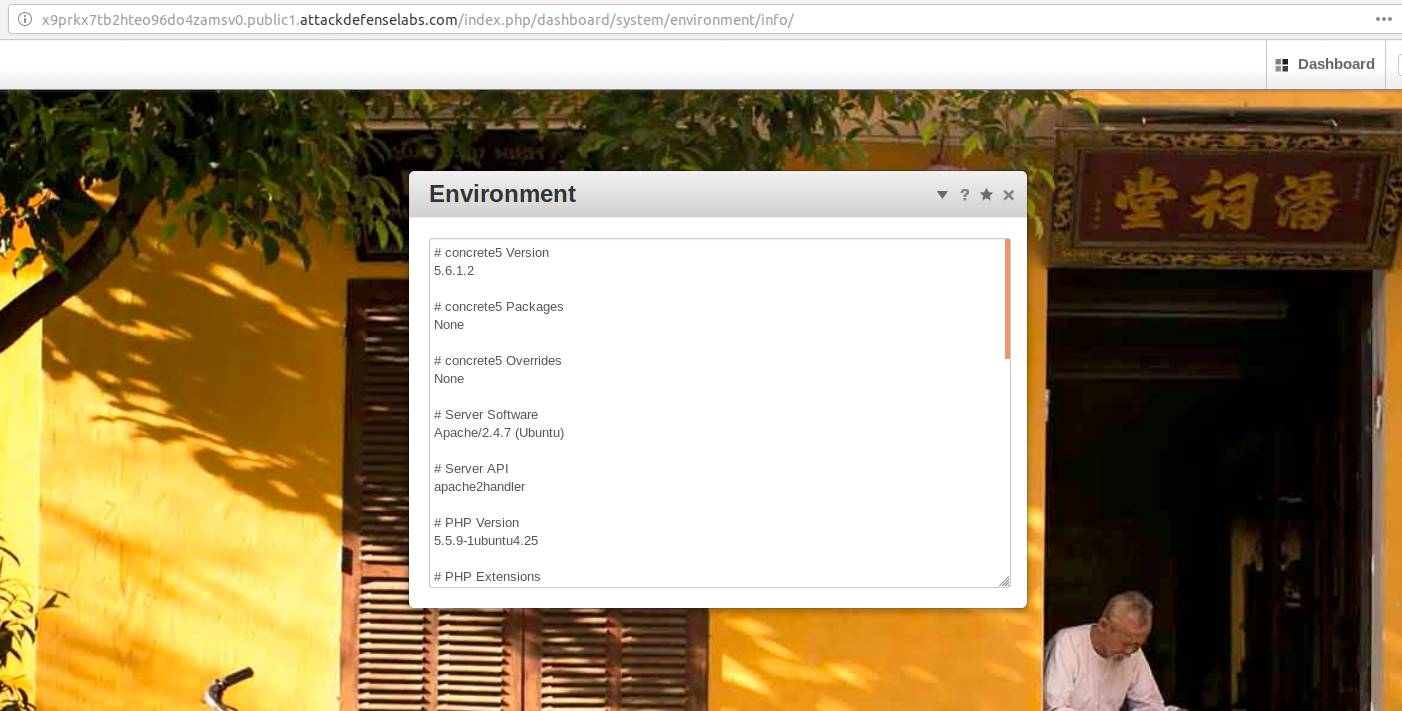
By navigating the application control panel, I have managed to obtain access to the environment variables on the following link.
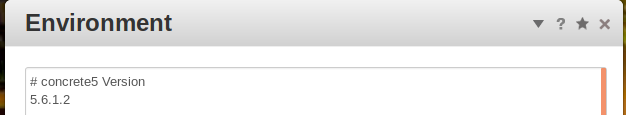
As we can see, the concrete5 Version is 5.6.1.2.
Again I will use @GetSploitBot for Telegram in order to obtain exploits for my version of concret5.
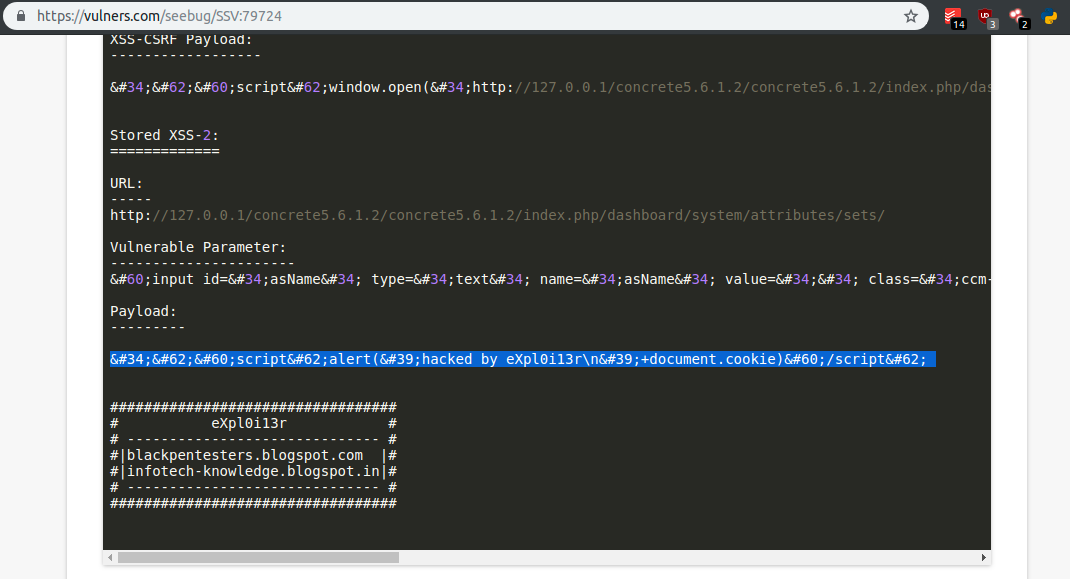
Following the above exploit, I was able to found the following path:
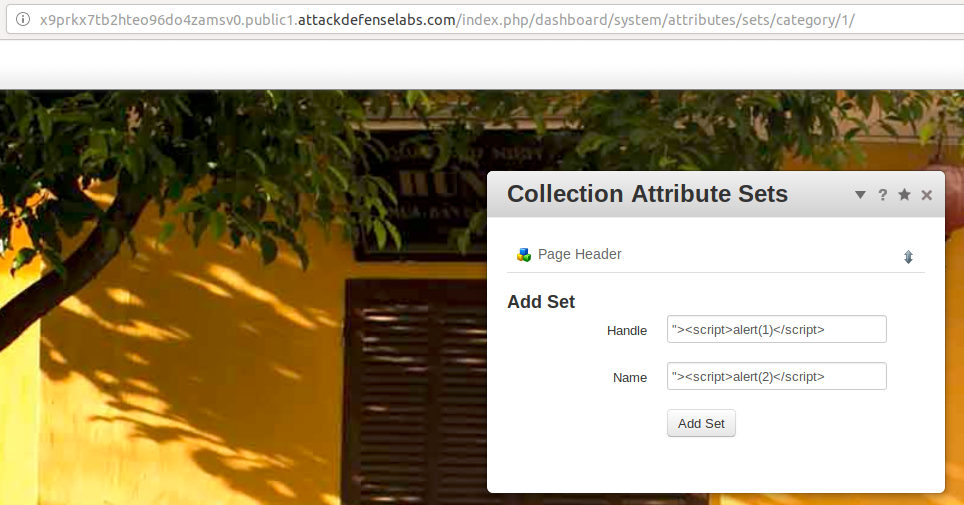
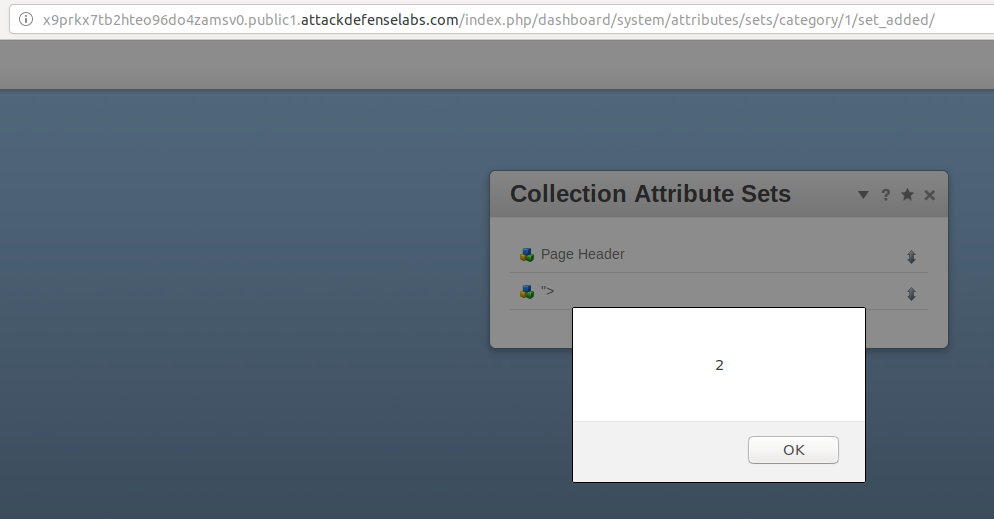
I decided to set my XSS payloads at http://x9prkx7tb2hteo96do4zamsv0.public1.attackdefenselabs.com/index.php/dashboard/system/attributes/sets/category/1/, as seen in the below example:
Result of my payloads: