Exploit Exercises: Nebula Level 08
World readable files strike again. Check what that user was up to, and use it to log into flag08 account. To do this level, log in as the level08 account with the password level08. Files for this level can be found in /home/flag08.
Source code
There is no source code available for this level
Solution
As usual let’s go to our flag account folder. I bet you will get bored of that at some point.
1
2
3
4
5
6
7
8
9
10
level08@nebula:~$ cd /home/flag08/
level08@nebula:/home/flag08$ ls -al
total 14
drwxr-x--- 2 flag08 level08 86 Aug 19 2012 .
drwxr-xr-x 1 root root 80 Aug 27 2012 ..
-rw-r--r-- 1 flag08 flag08 220 May 18 2011 .bash_logout
-rw-r--r-- 1 flag08 flag08 3353 May 18 2011 .bashrc
-rw-r--r-- 1 flag08 flag08 675 May 18 2011 .profile
-rw-r--r-- 1 root root 8302 Nov 20 2011 capture.pcap
level08@nebula:/home/flag08$
Hmm, for the first time it seems to be a pcap file!
1
2
3
level08@nebula:/home/flag08$ file capture.pcap
capture.pcap: tcpdump capture file (little-endian) - version 2.4 (Ethernet, capture length 65535)
level08@nebula:/home/flag08$
Definitely! But what is wireshark or tcpdump?
Wireshark is a network packet analyzer. A network packet analyzer will try to capture network packets and tries to display that packet data as detailed as possible.
You could think of a network packet analyzer as a measuring device used to examine what’s going on inside a network cable, just like a voltmeter is used by an electrician to examine what’s going on inside an electric cable (but at a higher level, of course).
In the past, such tools were either very expensive, proprietary, or both. However, with the advent of Wireshark, all that has changed.
Wireshark is perhaps one of the best open source packet analyzers available today.
And in other simpler words, tcpdump is the CLI (Command Line Interface) tool as Wireshark.
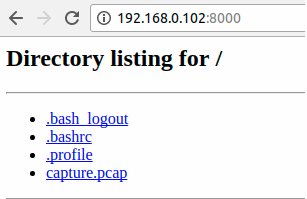
As you can see we have to open the “capture.pcap” file in a one of the above described tools and to get some information about our task. Personally I enjoy and know Wireshark, but here I can not install anything. Let’s make a simple HTTP server using python to retrive our file from the server.
1
2
level08@nebula:/home/flag08$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
level08@nebula:/home/flag08$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
192-168-0-104.myownisp.hacker - - [24/Oct/2017 12:57:43] "GET / HTTP/1.1" 200 -
192-168-0-104.myownisp.hacker - - [24/Oct/2017 12:57:43] code 404, message File not found
192-168-0-104.myownisp.hacker - - [24/Oct/2017 12:57:43] "GET /robots.txt HTTP/1.1" 404 -
192-168-0-104.myownisp.hacker - - [24/Oct/2017 12:57:43] code 404, message File not found
192-168-0-104.myownisp.hacker - - [24/Oct/2017 12:57:43] "GET /favicon.ico HTTP/1.1" 404 -
192-168-0-104.myownisp.hacker - - [24/Oct/2017 12:58:25] "GET /capture.pcap HTTP/1.1" 200 -
^CTraceback (most recent call last):
File "/usr/lib/python2.7/runpy.py", line 162, in _run_module_as_main
"__main__", fname, loader, pkg_name)
File "/usr/lib/python2.7/runpy.py", line 72, in _run_code
exec code in run_globals
File "/usr/lib/python2.7/SimpleHTTPServer.py", line 220, in <module>
test()
File "/usr/lib/python2.7/SimpleHTTPServer.py", line 216, in test
BaseHTTPServer.test(HandlerClass, ServerClass)
File "/usr/lib/python2.7/BaseHTTPServer.py", line 602, in test
httpd.serve_forever()
File "/usr/lib/python2.7/SocketServer.py", line 225, in serve_forever
r, w, e = select.select([self], [], [], poll_interval)
KeyboardInterrupt
level08@nebula:/home/flag08$
At this point I closed my HTTP server. Let’s see the file I have just downloaded.
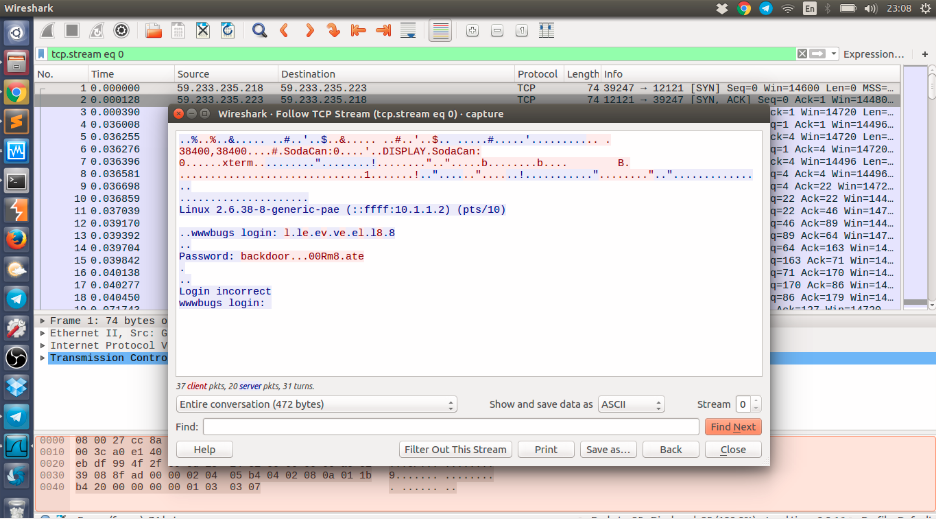
Right click on first packet > Follow > TCP Stream
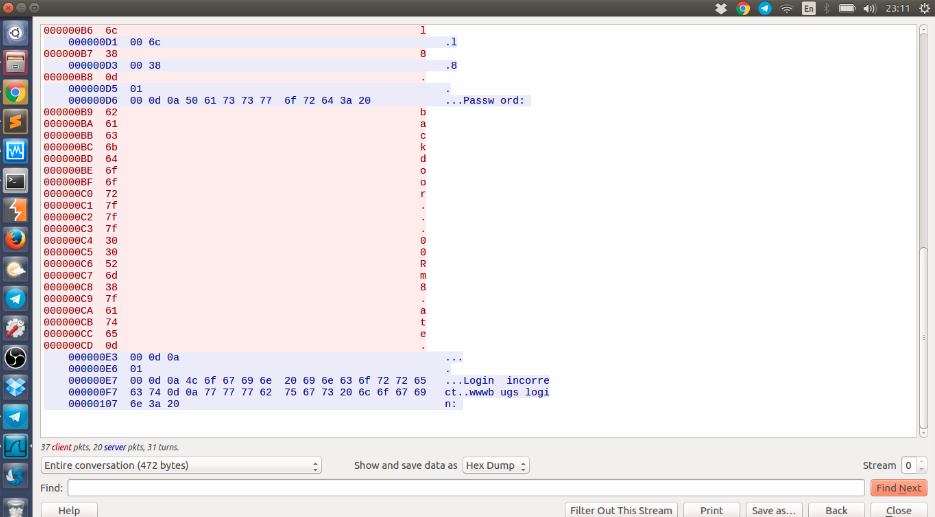
At this point you could try your luck with the given password, but you can be also smarter and interpret everything in hexa.
In other words:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
00000000 ff fd 25 ..%
00000000 ff fc 25 ..%
00000003 ff fb 26 ff fd 18 ff fd 20 ff fd 23 ff fd 27 ff ..&..... ..#..'.
00000013 fd 24 .$
00000003 ff fe 26 ff fb 18 ff fb 20 ff fb 23 ff fb 27 ff ..&..... ..#..'.
00000013 fc 24 .$
00000015 ff fa 20 01 ff f0 ff fa 23 01 ff f0 ff fa 27 01 .. ..... #.....'.
00000025 ff f0 ff fa 18 01 ff f0 ........
00000015 ff fa 20 00 33 38 34 30 30 2c 33 38 34 30 30 ff .. .3840 0,38400.
00000025 f0 ff fa 23 00 53 6f 64 61 43 61 6e 3a 30 ff f0 ...#.Sod aCan:0..
00000035 ff fa 27 00 00 44 49 53 50 4c 41 59 01 53 6f 64 ..'..DIS PLAY.Sod
00000045 61 43 61 6e 3a 30 ff f0 ff fa 18 00 78 74 65 72 aCan:0.. ....xter
00000055 6d ff f0 m..
0000002D ff fb 03 ff fd 01 ff fd 22 ff fd 1f ff fb 05 ff ........ ".......
0000003D fd 21 .!
00000058 ff fd 03 ff fc 01 ff fb 22 ff fa 22 03 01 00 00 ........ ".."....
00000068 03 62 03 04 02 0f 05 00 00 07 62 1c 08 02 04 09 .b...... ..b.....
00000078 42 1a 0a 02 7f 0b 02 15 0f 02 11 10 02 13 11 02 B....... ........
00000088 ff ff 12 02 ff ff ff f0 ff fb 1f ff fa 1f 00 b1 ........ ........
00000098 00 31 ff f0 ff fd 05 ff fb 21 .1...... .!
0000003F ff fa 22 01 03 ff f0 .."....
000000A2 ff fa 22 01 07 ff f0 .."....
00000046 ff fa 21 03 ff f0 ff fb 01 ff fd 00 ff fe 22 ..!..... ......"
000000A9 ff fd 01 ff fb 00 ff fc 22 ........ "
00000055 ff fa 22 03 03 e2 03 04 82 0f 07 e2 1c 08 82 04 .."..... ........
00000065 09 c2 1a 0a 82 7f 0b 82 15 0f 82 11 10 82 13 11 ........ ........
00000075 82 ff ff 12 82 ff ff ff f0 ........ .
0000007E 0d 0a 4c 69 6e 75 78 20 32 2e 36 2e 33 38 2d 38 ..Linux 2.6.38-8
0000008E 2d 67 65 6e 65 72 69 63 2d 70 61 65 20 28 3a 3a -generic -pae (::
0000009E 66 66 66 66 3a 31 30 2e 31 2e 31 2e 32 29 20 28 ffff:10. 1.1.2) (
000000AE 70 74 73 2f 31 30 29 0d 0a 0a 01 00 77 77 77 62 pts/10). ....wwwb
000000BE 75 67 73 20 6c 6f 67 69 6e 3a 20 ugs logi n:
000000B2 6c l
000000C9 00 6c .l
000000B3 65 e
000000CB 00 65 .e
000000B4 76 v
000000CD 00 76 .v
000000B5 65 e
000000CF 00 65 .e
000000B6 6c l
000000D1 00 6c .l
000000B7 38 8
000000D3 00 38 .8
000000B8 0d .
000000D5 01 .
000000D6 00 0d 0a 50 61 73 73 77 6f 72 64 3a 20 ...Passw ord:
000000B9 62 b
000000BA 61 a
000000BB 63 c
000000BC 6b k
000000BD 64 d
000000BE 6f o
000000BF 6f o
000000C0 72 r
000000C1 7f .
000000C2 7f .
000000C3 7f .
000000C4 30 0
000000C5 30 0
000000C6 52 R
000000C7 6d m
000000C8 38 8
000000C9 7f .
000000CA 61 a
000000CB 74 t
000000CC 65 e
000000CD 0d .
000000E3 00 0d 0a ...
000000E6 01 .
000000E7 00 0d 0a 4c 6f 67 69 6e 20 69 6e 63 6f 72 72 65 ...Login incorre
000000F7 63 74 0d 0a 77 77 77 62 75 67 73 20 6c 6f 67 69 ct..wwwb ugs logi
00000107 6e 3a 20 n:
Here you can observe that the “dots” are actually 0x7f in hexa which means “Backspace” in ASCII. So instead of “backdoor…00Rm8.ate” as password we have “backd00Rmate”. For the grand final:
1
2
3
4
5
6
7
8
9
level08@nebula:/home/flag08$ id
uid=1009(level08) gid=1009(level08) groups=1009(level08)
level08@nebula:/home/flag08$ su flag08
Password:
sh-4.2$ id
uid=991(flag08) gid=991(flag08) groups=991(flag08)
sh-4.2$ getflag
You have successfully executed getflag on a target account
sh-4.2$
See you in the next tutorial.
Sources
https://www.wireshark.org/docs/wsug_html_chunked/ChapterIntroduction.html